Mapping Active Directory, LDAP, and Workday Values in a SAML template
The Template SAML 2.0 app is deprecated. It's recommended that you use the SAML App Integration Wizard instead of the template app to create SAML integrations through the Admin Console. The wizard is more powerful and easier to use than the template. The ability to create app instances using templates may be restricted in the future. Existing apps that were created using templates are still supported. See Using the App Integration Wizard for more details.
When you integrate Okta with third-party SAML 2.0 service providers using the Template SAML 2.0 app, you can map Active Directory, LDAP, and Workday user values to SAML attributes. In addition to the standard Okta profile attributes (first name, last name, email, and Okta username), you can use other attributes that have been pulled into Okta from other sources.
To configure your Template SAML 2.0 app:
-
In the Admin Console, go to .
-
Click Browse App Catalog.
-
Search for and select Template SAML 2.0 App.
-
After configuring the General Settings for this app, select the Sign On tab and click View Setup Instructions.
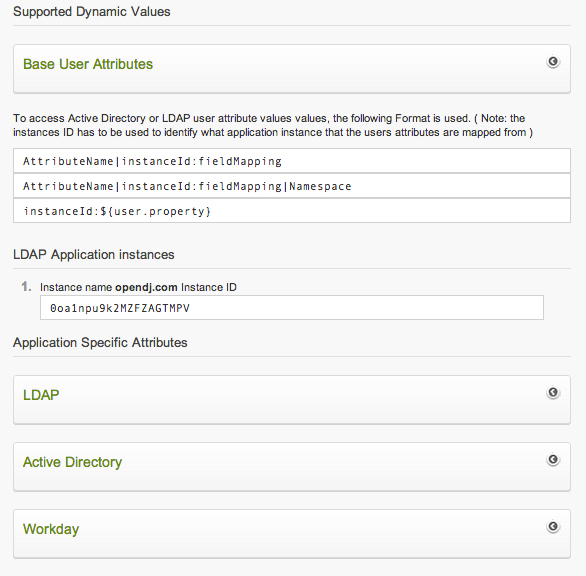
For a list of the supported values, select the Active Directory, LDAP, or Workday link on this page.
- Identify the instanceId for the repository that you want to use. The instanceId for your configured Active Directory, LDAP, and Workday instances are displayed. For example, the following image shows an LDAP instance with the ID 0oa1npu9k2M2FZAGTMPV. Use that instanceID for each attribute that's referenced in the mapping.
-
On the General tab of the Template SAML 2.0 app, configure the attribute statement field to map user values to SAML attributes. For each repository type (Active Directory, LDAP, and Workday), the attribute names and lists are slightly different. Make sure you use the corresponding attribute names for your repository. The Application Specific Attributes section provides a list of the Active Directory, LDAP, and Workday attribute names and formats that are available.
A SAML attribute can contain a maximum number of 1024 characters. The attribute formatting information isn't required. If you run out of space in an attribute statement, try removing the format statement for each attribute; for example urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified.

