Learn about the Okta IWA Web agent
The Okta IWA Web agent is a lightweight Internet Information Services (IIS) web agent that enables Desktop Single Sign-on (DSSO) on the Okta service. DSSO allows users to be automatically authenticated by Okta and any apps accessed through Okta, whenever they sign in to your Windows network.
The Okta IWA Web agent uses Microsoft's IWA and ASP.NET to authenticate users from specified gateway IPs.
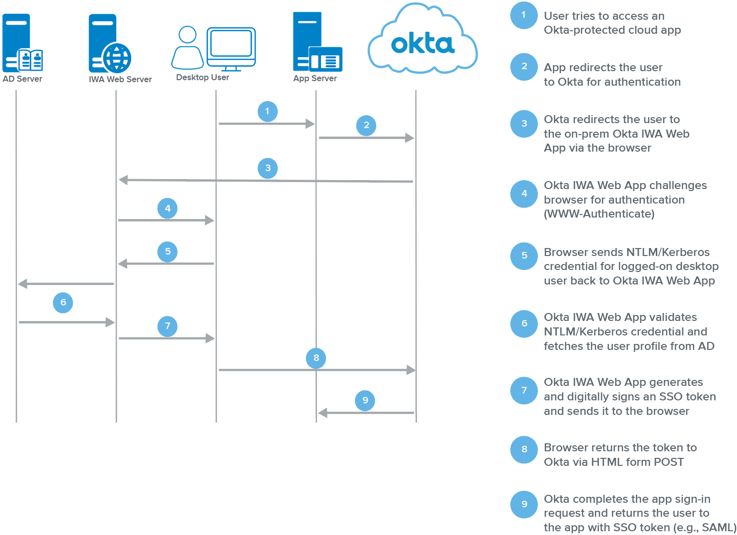
IWA Authentication Flow—Diagram 1
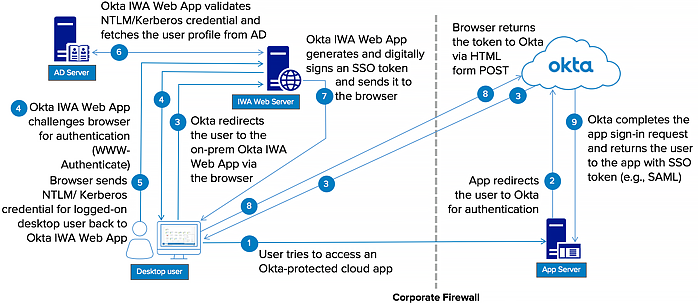
IWA Authentication Flow—Diagram 2
When you have only one forest it doesn't matter to which IWA agent requests are routed. When you have multiple forests, you need to start taking network configuration into consideration. Ensure that user A on machine A only redirects to IWA agents that are in forest A. Also ensure that user B on machine B only redirects to agents that are in forest B. The suggested way of doing that is redirecting the traffic from Okta to a global redirect URL, and then setting up your on-premises DNS to do the correct routing for that endpoint. You may also need to set up on-premises load balancing and the ability to detect which agents are online and offline into your load balancer.
Okta strongly recommends that you transition to using the Secure Sockets Layer (SSL) with the on-premises agent. This isn't only an important security provision, but it's also a hard requirement for application authentication (in particular, Windows 10 Universal Applications such as OneNote, Mail).
The latest builds of Office 2016 and Windows 10 are incorporating their Web Account Manager (WAM) for sign-in workflows (see this Microsoft article). WAM requires https — it blocks non-https traffic during auth workflows.
Refer to Configure SSL for the Okta IWA Web agent for details about how to configure IWA for this use case.
When re-enabling IWA DSSO, Identity Provider (IdP) routing rules must be manually reactivated.

