Customization options for inbound SAML
You have several customization options when you connect users to Okta with inbound SAML.
- Your users can SSO into Okta with no additional provisioning because the users are sourced in Okta.
- The inbound Identity Provider (IdP) can provision users to Okta with Just-In-Time (JIT) provisioning. A toggle allows you to enable and disable JIT provisioning on a per-IdP trust basis.
- Your users can be assigned to groups with JIT.
- You can enable or disable automatic account linking between SAML IdPs and Okta. You can also restrict automatic account linking based on whether the Okta user is a member of any specified groups.
Because inbound SAML is built on Universal Directory (UD), you can store rich attributes in Okta from incoming assertions. Define as many Identity Providers as you need, and then define an unlimited number of attributes for each provider using the Profile Editor. You aren't limited to just the first name, family name, email, and phone attributes.
Okta also supports encrypted assertions, shared ACS URL or a trust-specific ACS URL, and configurable clock skew.
The following table shows configurable signature-algorithm requirements for inbound SAML.
|
Supported algorithms |
Description |
|---|---|
| Encryption |
Inbound SAML transparently supports encrypted SAML assertions. The IdP can encrypt using the public certificate from Okta and any of the following XML encryption algorithms. |
| Digest | |
|
Signature |
|
|
Canonicalization |
|
|
Transform |
Setup information
Certain information that you need to complete the setup may not be available at the time that you're filling in the form. The following chart shows a typical information flow.
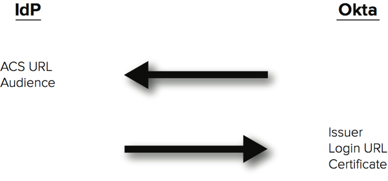
For example, when you're setting up the IdP in Okta, sometimes the Issuer, Login URL, and Certificate aren't available from the IdP until the ACS URL and Audience are set up in the IdP. That information is also not available until Okta is configured.
Setup recommendation
If the IdP requires information from Okta for setup before you have the information, enter any text for the Issuer in Okta and enter https:url for the Login URL in Okta. Add the Identity Provider in Okta. Then, use the ACS URL and Audience that become available in Okta to set up the IdP. Finally, edit the IdP that you just set up in Okta, and enter the appropriate issuer and login URL information.

