System Log events for Okta ThreatInsight
Okta ThreatInsight records requests from potentially malicious IP addresses in the System Log. It records the following types of events:
- Sign-in attempts from suspicious IP addresses
- Security threat detected
- Org Under Attack
View System Log events
-
In the Admin Console, go to .
- Under Okta ThreatInsight settings, click System Log. The search field is pre-populated with the query eventType eq "security.threat.detected". You can customize this query to find other types of events.
- Configure the date range.
- Click the magnifying glass icon beside the Search field.
Sign-in attempts from suspicious IP addresses
If Okta ThreatInsight detects sign-on attempts from a potentially suspicious IP address, it sets the ThreatSuspected field to true.
Paste this query into the System Log Search field to find sign-in attempts from suspicious IP addresses:
debugContext.debugData.threatSuspected eq "true"
The ThreatSuspected field also appears in the user.session.start and security.threat.detected System Log events.
Security threat detected
The security.threat.detected event only appears in the System Log if a request is deemed a high threat.
Okta ThreatInsight evaluates sign-in activity before the user can be identified, so security.threat.detected events don't include a username.
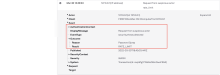
The outcome.result field describes how Okta ThreatInsight handled the request:
- DENY: Okta ThreatInsight terminated the request to prevent malicious actors from consuming the rate limit for your org.
- RATE_LIMIT: Okta ThreatInsight detected suspicious activity.
- ALLOW: Okta ThreatInsight allowed the request to proceed. To find other events with the same transaction ID, enter this query in the search field: transaction.id eq "<TRANSACTION_ID>". The actor field displays the username associated with the request.
The outcome.reason field displays the reason for the result.
Here's an example of a System Log event with a result of DENY:
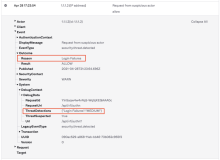
Here's an example of a System Log event with a result of RATE_LIMIT:
Org Under Attack
When an org is under attack, Okta ThreatInsight flags IP addresses more aggressively. This can result in more security.threat.detected events appearing in the System Log.
Paste these queries into the System Log Search field to find Org Under Attack events:
- eventType eq "security.attack.start"
- eventType eq "security.attack.end"
The outcome.reason field displays the reason for the result.
Here's an example of a System Log event that was flagged as medium risk because of sign-in failures:
Add potentially malicious IP addresses to a blocklist
Once you have found System Log events that might indicate malicious activity, you can add the IP addresses associated with them to a blocklist.
The IP address appears at the top of the event under the Actor column:
See Blocklist network zones for instructions.