Configure optional settings
Fortinet supports tw optional settings: Client IP Reporting and Groups response.
Topics:
Before you begin
- Ensure that you have the common UDP Port and Secret key values available
Configure Client IP Reporting
To configure Okta to be able to parse, report on and eventually enforce policy based off of the source client IP Address you need to configure the Fortinet Fortigate (RADIUS) App in Okta as follows:
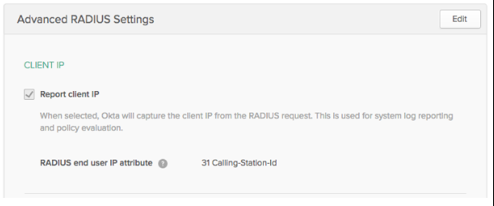
Enter the following settings in Advanced RADIUS Settings found on the Sign On tab for the RADIUS app in your Okta Admin Console, as shown below.
- Client IP: Check Report client IP.
- RADIUS End User IP Attributes: 31 Calling-Station-Id
Configure Groups Response
The Fortinet appliance does not receive groups using the standard Attribute Value Pairs (AVP) of 11 (Filter-Id) and 25 (Class). Instead it relies on Vendor Specific Attributes.
To configure the app to send RADIUS group information in vendor-specific attributes, complete the following steps:
-
In the Admin Console, go to .
- Find the application using the Search field and then click its name in the search results.
- Select the Sign on tab.
- Scroll to the Advanced RADIUS Settings section and then click Edit.
- In the Groups Response section, complete the following options:
- Select Include groups in RADIUS response.
- In the RADIUS attribute subsection, select 26-Vendor specific.
- In the Vendor Specific ID field, enter the numeric vendor ID code for your product:
- Cisco ASA-Group-Policy: 3076
- Citrix Group-Names: 3845
- Fortinet Group-Name: 12356
- Palo Alto User-Group: 25461
If your vendor-specific ID doesn't appear here, search for it in the documentation for your product.
- In the Attribute ID field, enter the numeric attribute ID for your product:
- Cisco ASA-Group-Policy: 25
- Citrix Group-Names: 16
- Fortinet Group-Name: 1
- Palo Alto User-Group: 5
If your attribute ID doesn't appear here, search for the group policy attribute in the documentation for your product.
- Click Save.
The maximum length of the group membership value is 247 bytes. If the group name length exceeds this limit, it's truncated and partial values are returned. Configure the response as a set of repeated attributes instead of using a single delimited list.

