Enhance Windows Device Trust security with Trusted Platform Module (TPM)
This document describes how to leverage the security benefits of the Trusted Platform Module (TPM) by installing Okta Device Registration Task version 1.4.1 or later on your domain-joined Device Trust-secured Windows computers with TPM 1.2 or 2.0. Use this document in conjunction with the main Okta Device Trust document for Windows, Enforce Okta Device Trust for managed Windows computers.
TPM is a microchip built into most Windows computers. It is designed to provide tamper-resistant security functions, primarily involving encryption keys. When used with the Okta Device Trust solution for Windows computers, TPM prevents malicious actors from copying the Private Key from Windows devices. If TPM is present and enabled on the device, installing Okta Device Registration Task version 1.4.1 or later generates a hardware-based key used by the Okta Device Trust solution for Windows computers. If a device lacks TPM, or if you install Registration Task version 1.4.1 or later using the method that skips support for TPM (described below), the Registration Task generates a software-based key (pre-1.4.1 behavior).
Prerequisites
- Okta Device Registration Task 1.4.1 or later
- Windows domain-joined computers
- Windows 8 and 10, 32- and 64-bit
- Internet Explorer, Edge, and Chrome browsers
- TPM is enabled, activated, and owned. For definitions of these terms, see the Microsoft document TPM Fundamentals.
- Windows 10 computers running v1803 Build 17134.254 or earlier must have Cumulative Update KB4346783
- TPM security benefits will not take effect on Windows devices already enrolled in this Device Trust solution until the certificate is renewed
- For some Windows computers, it may be necessary to enable TPM in the BIOS (though it is typically enabled by default). If TPM is not enabled, the Okta Device Registration Task generates a software-based key instead of a hardware-based key.
You can use GPO to centrally configure several TPM Services.
Procedures
Perform the procedure to obtain and install the Device Registration Task. Perform the other procedures if appropriate for your implementation.
Obtain and install the Device Registration Task
- In the Admin Console, go to , scroll to Okta Device Trust Windows Agents, and download Okta Device Registration Task version 1.4.1 or later.
- Install the registration task as described in Enforce Okta Device Trust for managed Windows computers.
Make sure to read the information about proxy servers and certificate handling in Enforce Okta Device Trust for managed Windows computers.
If your Windows 10 computers are running v1803 Build 17134.254 or earlier, you must install Cumulative Update KB4346783. The update "Addresses an issue where Microsoft Edge or other UWP applications can't perform client authentication when the private key is stored on a TPM 2.0 device." (See the Microsoft article KB4346783 (OS Build 17134.254)). Without the update, users with trusted Windows computers aren't able to access device trust-secured UWP apps or Edge.
Install the Device Registration Task without the TPM security enhancement (optional)
You can install version 1.4.1 with or without enabling TPM security enhancements. Either way, version 1.4.1 provides the following fixes:
- Fixes an issue that caused Chrome browser settings to be removed when the Device Registration Task was uninstalled.
-
Fixes an issue where uninstalling the Device Registration Task removed the automatic certificate selection setting in Chrome. The setting is designed to prevent the browser from prompting end users to select the certificate during the device trust flow.
If you don't want to leverage the TPM security benefits enabled by Okta Device Registration Task version 1.4.1, you can include the argument SkipTPM=true in the installation command as shown below:
OktaDeviceRegistrationTaskSetup.exe /q2 OktaURL=<URL> SkipTPM=trueCheck the status of the TPM (optional)
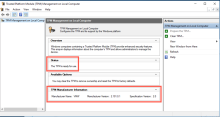
It may be useful to check the status of TPM. To do so, open the TPM Management console either from a command prompt or the Start menu.
- From a command prompt, enter TPM.msc
- From the Start button search field, enter TPM
Known issues
- TPM security is not implemented when Okta Device Registration Task 1.4.1 is installed on Windows 7 computers – Version 1.4.1 works with Windows 7 computers but without TPM security enhancements. A software-based key is generated instead of a hardware-based key. Additionally, version 1.4.1 provides other fixes unrelated to TPM security.
- Update necessary for Windows 10 machines running v1803 Build 17134.254 or earlier.
If your Windows 10 computers are running v1803 Build 17134.254 or earlier, you must install Cumulative Update KB4346783. The update "Addresses an issue where Microsoft Edge or other UWP applications can't perform client authentication when the private key is stored on a TPM 2.0 device." (See the Microsoft article KB4346783 (OS Build 17134.254)). Without the update, users with trusted Windows computers aren't able to access device trust-secured UWP apps or Edge.
- You must manually delete the old certificate if you are reverting from Device Registration Task 1.4.0 to 1.3.1 – Otherwise, the following exception is thrown: Invalid provider type specified.
Delete the certificate manually
- Go to Start and enter mmc in the search field to open the console.
- Go to File and click Add/Remove Snap-in.
- Select Certificates and then click Add.
- In the Certificates snap-in dialog box, select My user account.
- Click Finish.
- Click OK.
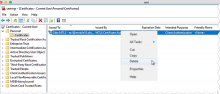
- Under Console Root, expand Certificates - Current User.
- Expand the Personal folder, click Certificates, right-click the Okta MTLS certificate, and then choose Delete.
Related topics
Enforce Okta Device Trust for managed Windows computers