Step 1: Configure VMware Identity Manager as an Identity Provider in Okta
This section describes how to configure VMware Identity Manager as an identity provider (IdP) in Okta. This configuration is required to configure a unified catalog as well as mobile SSO and device trust.
For additional information, see Add a SAML 2.0 IdP section of the Okta Identity Providers documentation.
Get VMware Identity Manager SAML Metadata Information
Retrieve the SAML metadata information from VMware Identity Manager that is required to set up an identity provider in Okta.
- Log in to the VMware Identity Manager console as the System administrator.
- Select the tab.
- Click Settings.
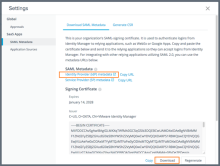
- Click SAML Metadata in the left pane.
The Download Metadata tab is displayed.
- Download the Signing Certificate.
- In the Signing Certificate section, click Download.
- Make a note of where the certificate files is downloaded (signingCertificate.cer).
- Retrieve the SAML metadata.
- In the SAML Metadata section, right-click the Identity Provider (IdP) metadata link and open it in a new tab or window.
- In the identity provider metadata file, find and make a note of the following values:
- entityID
For example: https://tenant.vmwareidentity.com/SAAS/API/1.0/GET/metadata/idp.xml
- SingleSignOnService URL with Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST"
For example: https://tenant.vmwareidentity.com/SAAS/auth/federation/sso
- entityID
Add an Identity Provider in Okta
For additional information about how Okta handles external identity providers, see Identity Providers.
- In the Okta Admin Console, go to .
- Click Add Identity Provider and select SAML 2.0 IdP.
- Click Next.
- Enter a name for the identity provider. For example, Workspace ONE.
- Configure the following:
- IdP Username: Enter idpuser.subjectNameId.
If you plan to send the username in a custom SAML attribute, define an appropriate expression. For information, see Okta Expression Language.
- Filter: Do not select this checkbox.
- Match against: Select Okta Username.
Adjust the selection as required for your environment and the values that you plan to send.
- If no match is found: Select Redirect to Okta sign-in page.
- IdP Issuer URI: Enter the entityID.
This is the value you obtained from the identity provider metadata file from Workspace ONE. For example, https://tenant.vmwareidentity.com/SAAS/API/1.0/GET/metadata/idp.xml
- IdP Single Sign-On URL: Enter the SingleSignOnService Location URL.
This is the value you obtained from the identity provider metadata file from Workspace ONE. For example, https://tenant.vmwareidentity.com/SAAS/auth/federation/sso
- IdP Signature Certificate: Browse and select the Signing Certificate file you downloaded from Workspace ONE in Get VMware Identity Manager SAML Metadata Information.
- Request Authentication Context: Select Device Trust.
- IdP Username: Enter idpuser.subjectNameId.
- Click Finish.
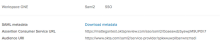
- Verify that the following information appears:
- SAML Metadata
- Assertion Consumer Service URL
- Audience URI
-
Download and save the metadata file.
Click the Download Metadata link.
Save the metadata file locally.
Open the metadata file and copy its contents for use in Get VMware Identity Manager SAML Metadata Information.