Configure the VMware Horizon View Connection Server
During this task we will configure the VMware Horizon View Connection Server to use the Okta RADIUS Server Agent as a RADIUS Authenticator.
Steps
Configuration of the VmWare Horizon View Connection server includes:
Before you begin
- Ensure that you have the common UDP port and secret key values available.
Defining a RADIUS Authenticator
- Sign in to the VMware Horizon Administrator console with sufficient privileges.
- Navigate to , and highlight the connection server to work with.
- Click Edit in the top submenu.
- In the dialog that opens, select the Authentication tab.
- Scroll down to the Advanced Authentication section.
- Set the 2-factor authentication value to RADIUS.
- Click the Manage Authenticators button.
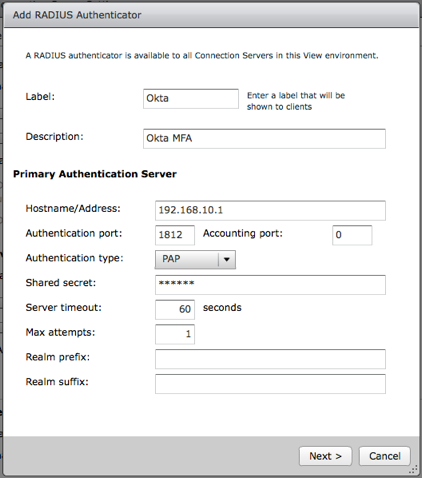
- In the dialog that opens, click Add. The screen below displays.
-
Enter values, as shown:
- Label: Enter a unique label.
- Description: Enter an option description.
- Hostname/Address: IP or Name of Okta RADIUS Server Agent
- Authentication port: Port configured in step x (1812)
- Accounting port: 0
- Authentication type: PAP
- Server timeout: 60
- Max attempts: 1
- Realm prefix: Optional see username assignment value
- Realm suffix: Optional see username assignment value
- Click Next.
- Optionally, you can configure a Secondary Authentication Server, using the same settings in step 9 above with a different label and description.
- Click Finish to save all settings.
Configuring Advanced Authentication Settings
Advanced authentication settings are used to control the behavior that the View Connection Server uses and enforces. Once enabled, the View Connection server performs authentication against the two-factor authentication first. User experiences can differ.
If you force two-factor and Windows user name matching, the VMware Horizon View (RADIUS) application username value (set in Part 2, above) must match your Active Directory username, including any Realm prefix and Realm suffix values.
-
Enforce two-factor and Windows user name matching
This feature is usually enabled. One situation in which you may choose to disable this feature is to allow these usernames to differ so users can perform their initial authentications using their own Okta credentials and then sign in to Windows/AD using a shared or common account.
The screen shot below uses this configuration.
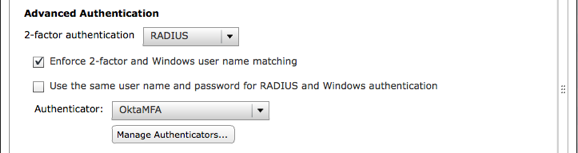
In this flow the VMware Horizon View (RADIUS) application MUST have its RADIUS Authentication Behavior configured so that Okta performs primary authentication is unchecked.
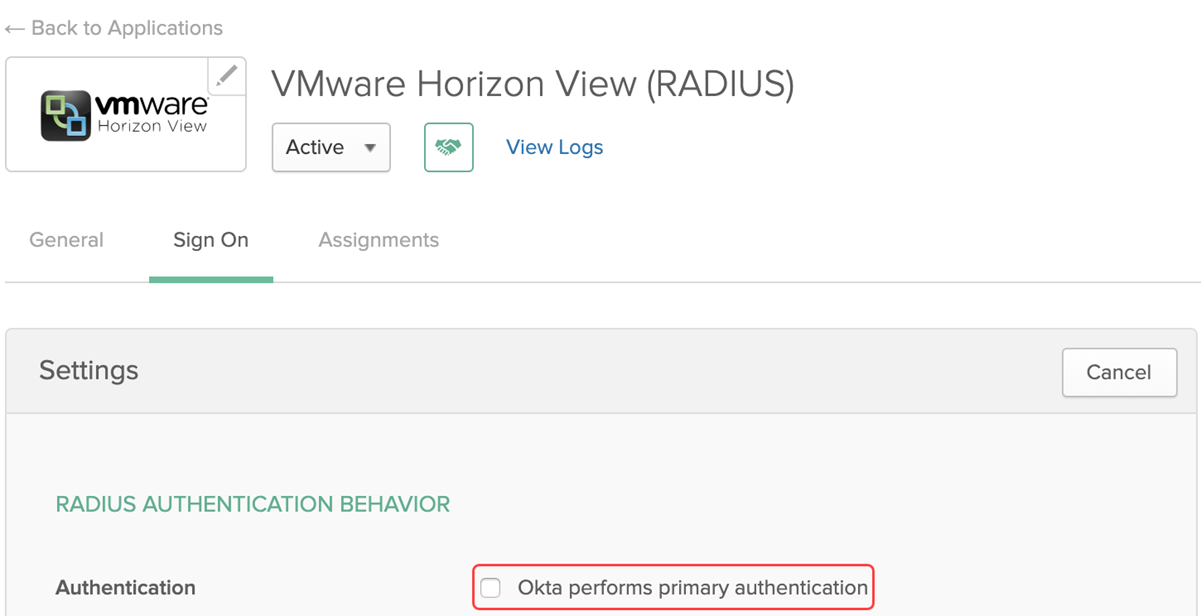
Tests 2 and 4 in the testing section.
- Use the same user name and password for RADIUS and Windows authentication
If you enable this setting, the Okta password and Windows/AD Password for the user must match, and the VMware Horizon View (RADIUS) application must be configured to perform primary authentication. You can use this setting when Okta is performing delegated authentication for users.
If you disable this setting, the Okta username can be different than the Windows/AD username and the VMware Horizon View (RADIUS) application can be configured to NOT perform primary authentication making the Okta password irrelevant.
The screen shown below uses this configuration.
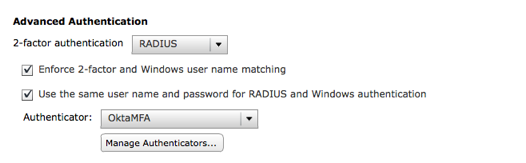
In this flow the VMware Horizon View (RADIUS) application MUST have its RADIUS Authentication Behavior configured so that Okta performs primary authentication is checked.
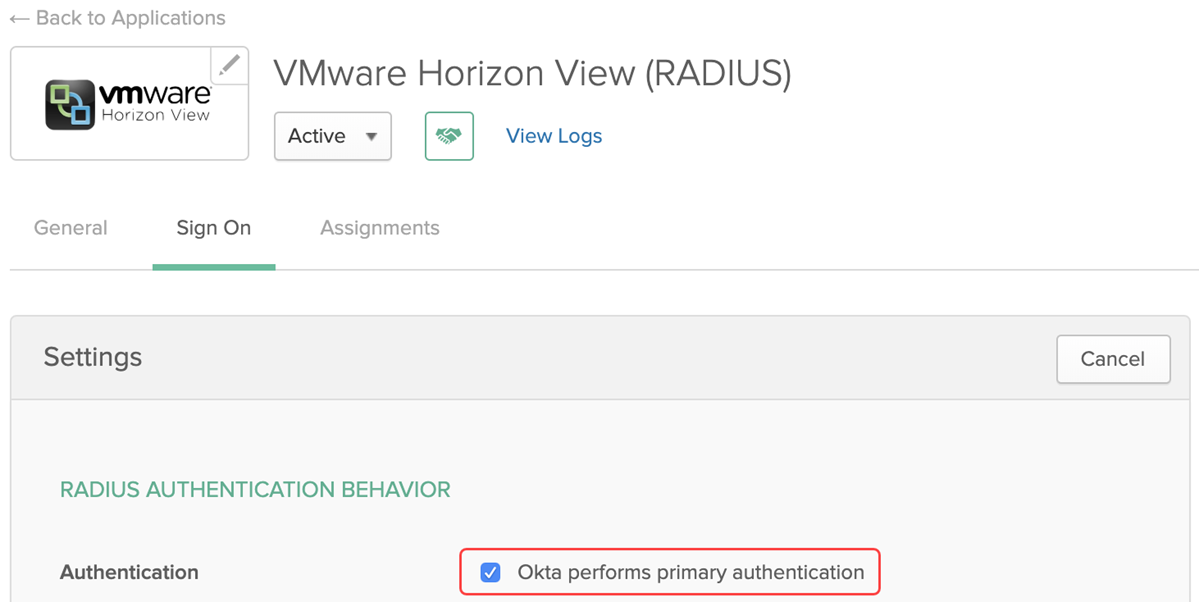
Tests 1 and 3, in the testing section.
The values you select for these two options change the sign in experience and dictate what settings you can configure in Okta.

