Create API access claims
Tokens contain claims that are statements about the subject or another subject, for example name, role, or email address.
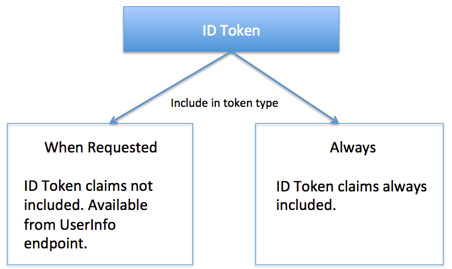
ID token claims are dynamic. By default, the authorization server doesn't include them in the ID token when requested with an access token or authorization code. To keep this default, select Userinfo/id_token request for Include in token type.
To force the Authorization server to always put a claim into the ID token, select Always for Include in token type.
If the claim isn't included, the client must use an access token to get the claims from the UserInfo endpoint.
- Choose the name of the authorization server to display it, and choose Claims. Okta provides a default subject claim. You can edit the mapping, or create your own claims.
-
Choose Add Claim and provide the requested information.
-
Name
-
Include in token type: Select Access Token (OAuth 2.0) or ID Token (OpenID Connect). For ID tokens, in the second dropdown choose Always or Userinfo/id_token request.
-
Value type: Choose whether the values defined in the claim use a Group filter or an Expression written using the Okta Expression Language.
-
Mapping: Appears if you choose Expression. Add the mapping here using the Okta Expression Language, for example
appuser.username. Be sure to check that your expression returns the results expected. The expression isn't validated here. -
Filter: Appears if you choose Groups. Use it to add a group filter. If you leave it blank, then this claim includes all users.
-
-
Disable claim: Check this option to temporarily disable the claim for testing or debugging.
-
Include in: Specify whether the claim is valid for any scope, or select the scopes for which it's valid.
-
While in the Claims list, you can:
- Sort claims by type.
-
Delete claims that you've created, or disable claims for testing or debugging purposes.


