Secure Office 365 using app sign-on policies
Before you begin
Complete Assign Office 365 to users and groups.
Start this task
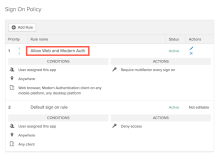
The default sign-on rule for Office 365 is different than other apps in Okta. This rule denies access to all clients from any network. It cannot be modified. This prevents clients that use Legacy Authentication from accessing Office 365.
The other Okta-provided rule allows access to only web browsers and apps that support Modern Authentication. Modern authentication is a term for a combination of authentication and authorization methods. These methods can include multifactor authentication (MFA), client certification-based authentication, Microsoft Entra ID Authentication Library (ADAL), and Open Authorization (OAuth).
You can edit this rule to make it more stringent. Alternatively, you can add another to allow clients using Legacy Authentication (not recommended).
Edit sign-on rule to prompt for MFA
You can edit Allow Web and Modern Auth rule to prompt for MFA.
Prerequisite
Factor types should be enabled before you can use them for the MFA prompt.
See Multifactor Authentication.
- Go to .
- From the Sign on Rule dialog, go to .
- Select the frequency at which you want to prompt the user for MFA when accessing Office 365.
- Click Save.
- In , select any of the 2 factor types options.
- Configure other options in the section.
- Select the appropriate Re-authetication frequency.
- Click Save.