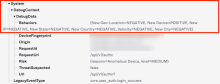
Behavior Detection System Log events
If sign-in attempts are evaluated for changes in behavior, details about the behavior detected are recorded in System Log events. Behavior Detection only tracks sign-in events with unique session context.
To see behavior details for user.session.start and policy.evaluate.sign_on events, go to DebugContext and DebugData. For example:
The Behaviors fields have entries in the form of key=value pairs. The key represents the behavior type and the value represents the outcome of the behavior evaluation.
These are the possible outcomes for behavior evaluation:
|
Value |
Description |
|---|---|
| POSITIVE | A change in behavior was detected. If MFA is configured for a policy rule and the behavior evaluated is POSITIVE, Okta prompts for MFA. |
| NEGATIVE | No change in behavior is detected. If MFA is configured for a policy rule and the behavior evaluated is NEGATIVE, Okta doesn't prompt for MFA. |
| UNKNOWN | Not enough history to detect behavior. If MFA is configured for a policy rule and the behavior evaluated is UNKNOWN, Okta prompts for MFA. |
| BAD_REQUEST | Not enough information from the sign-in attempt to detect behavior. For example, if the location can't be determined or a no device identifier was provided, the evaluation is reported as a BAD_REQUEST. If MFA is configured for a policy rule and the behavior evaluated is BAD_REQUEST, Okta prompts for MFA. |