Enable SAML or OIDC authentication for supported apps
SAML and OIDC are authentication protocols that reduce reliance on password-based authentication.
- SAML is an XML-based standard for exchanging authentication and authorization data between an Identity Provider (IdP) and a service provider (SP).
- OpenID Connect (OIDC) is a protocol that sits on top of the OAuth 2.0 framework. The OIDC protocol allows otherwise different systems to interoperate and share authentication state and user profile information.
- SWA is an SSO system developed by Okta to provide single sign-on for apps that don't support proprietary federated sign-on methods or SAML. In a SWA login, the username and password are passed to the third-party app whereas with SAML and OIDC, those credentials never leave Okta.
For more information, see App integrations.
HealthInsight task recommendation
Use SAML and OIDC authentication protocols for supported apps to reduce reliance on password-based authentication.
| Okta recommends |
Enable SAML or OIDC and disable SWA for applications when possible. |
| Security impact |
High |
| End-user impact |
None When signing in to their org, end users are prompted to enroll in required factors and may enroll in any factors set to optional. Factors that have been disabled aren't visible to end users. |
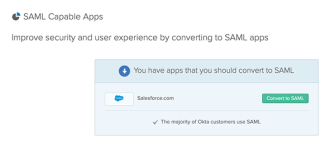
View a list of SAML-capable apps
-
In the Admin Console, go to .
- Under Application Usage, click SAML Capable Apps.
- Generate a report to see a list of available apps that can be converted to SAML.
- To convert an app to be SAML or OIDC capable, click Convert to SAML.
- Click Edit.
- Change the SSO method to SAML or OIDC and follow the on-screen instructions to convert your app successfully.