Enforce a limited session lifetime for all policies
The session lifetime determines the maximum idle time of a user's Okta session, and when the session expires.
Shorter session lifetimes reduce the risk of malicious parties gaining access to a user's session.
The default session lifetime is two hours. A countdown timer appears to users when there are five minutes of session time remaining.
HealthInsight task recommendation
Enforce a limited session lifetime in your org policies to reduce the risk of malicious access to a user's applications.
| Okta recommends |
A session lifetime of two hours or less. |
| Security impact |
High |
| End-user impact |
Moderate A countdown timer appears to users when there are five minutes of session time remaining. |
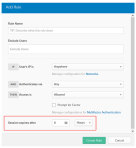
Set the session lifetime for a policy
-
In the Admin Console, go to .
- Click Sign On.
- Click Add Rule or Edit to modify an existing policy rule.
- Under Session expires after, set the session lifetime duration in minutes, hours, or days.
- Click Create Rule or Save Rule once your changes have been made.