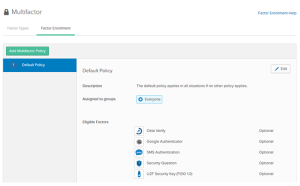
Disable weaker MFA factors in factor enrollment policies
Admins can configure multifactor authentication (MFA) at the organization level or application level. When users sign in to Okta or an app, they're prompted to authenticate themselves. If you deploy strong factors, they provide better protection against phishing, adversary-in-the-middle attacks, and others.
HealthInsight task recommendation
Enable strong MFA factors to improve resistance to phishing and man-in-the-middle attacks.
| Okta recommends |
Update factor enrollment policies based on the following:
|
| Security impact |
High |
| End-user impact |
High When signing in to their org, end users are prompted to enroll in required factors and may enroll in any factors set to optional. Factors that have been disabled aren't visible to end users. |
Enable strong factors for factor enrollment
-
In the Admin Console, go to .
- Click Factor Enrollment.
- Click Edit.
- Set the factor of your choice to Required, Optional, or Disabled.
The factor must be disabled in all factor enrollment policies before the factor type can be deactivated from the Factor Type tab.