Step 2: Configure Okta application source in VMware Identity Manager
Prerequisites
Step 1: Configure VMware Identity Manager as an Identity Provider in Okta
This step configures VMware Identity Manager to send device posture information in the SAML response to Okta after the user is authenticated.
This is a one-time, initial configuration task.
Configure Okta application source in VMware Identity Manager
Prerequisites
You have configured VMware Identity Manager as an identity provider in Okta as described in Step 1: Configure VMware Identity Manager as an Identity Provider in Okta.
Procedure
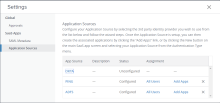
- In the VMware Identity Manager console, select the tab.
- Click Settings.
- Click Application Sources in the left pane.
- Click OKTA.
- In the OKTA Application Source wizard Definition page, enter a description if needed, then click Next.
-
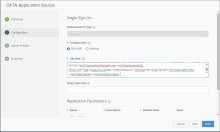
In the Configuration page:
- For Configuration, select URL/XML.
- In the URL/XML text box, copy and paste the SP metadata that you downloaded from Okta as described in Add an Identity Provider in Okta
- If you plan to configure device trust for iOS and Android mobile devices, click Advanced Properties and set the following options to Yes.
These properties are mandatory for the device trust solution for iOS and Android devices.
Option Description Device SSO Response Sends device posture information in the SAML response to Okta after the user is authenticated. Enable Force Authn Request Enable Force Authn request. The service provider can send the forceAuthn=true flag in the SAML request, which forces the user to be reauthenticated. Enable Authentication Failure Notification Receive SAML response error messages when authentication fails. - Click Next.
-
In the Access Policies page, select the default access policy set.
Authentication requests from Okta applications will be authenticated using this policy set.
- Click Next, review your selections, and then click Save.
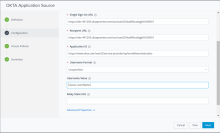
- Click the OKTA Application Source again.
- In the Configuration page, modify the Username Value to match the value that Okta is matching against, such as Okta Username.
- Click Next twice and then Save to save your changes.
Assign Okta application source to all users
Optional: You can allow end users to access apps from either the Okta dashboard or the Workspace ONE dashboard. Both experiences are fully supported. You can configure the Workspace ONE catalog to publish applications federated through Okta without the need to first import them into VMware Identity Manager.
For details, see Publish Okta apps to the Workspace ONE catalog