Troubleshoot Cisco Meraki integrations
Troubleshoot the Cisco Meraki integration.
General certificate error
This type of error occurs in the following situations:
- The CA certificate wasn't added on the client machine
- The wrong CA certificate was added on the client machine
- An incorrect Wi-Fi network is used
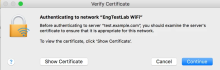
Extended key usage set certificate error
Description
Configuration appears correct when compared with Configure Cisco Meraki. However, a WiFi or VPN connection doesn't get established.
Symptoms
- The following log statement is visible in the RADIUS agent logs at the DEBUG level: DEBUG - ...finished handshake - will transfer app data
- One of the following error codes are present in the supplicant logs: 0x80090349 (-2146892983 SEC_E_CERT_WRONG_USAGE) 0x80420101 (-2143158015 EAP_E_USER_CERT_INVALID)
- One or more of the following error messages are present in the supplicant logs: The user {user} dialed a connection named {connection-name} which has failed. The error code returned on failure is -2146892983 Reason: Explicit Eap failure received Error: 0x80420101 EAP Reason: 0x80090349 EAP Root cause String: EAP Error: 0x80420101.
Solution
- Replace the current certificate with a new updated certificate.
- Examine and updated the Extended Key Usage(EKU) attributes as required.
RADIUS agent logging level
To set the log level in the RADIUS agent:
- Using a text editor, open the log4j.properties file from the installation folder C:\Program Files (x86)\Okta\Okta RADIUS Agent\current\user\config\radius\
- Change the last instance of info to debug (verbose) or trace (very verbose).
The update should resemble these example:
log4j.rootLogger=debug, app, stdoutThis is another example:
log4j.rootLogger=trace, app, stdout - Save the change and close the editor.
Examine logs or capture packets
To examine logs or capture packets:
- On Mac, to display log information during connection attempts:
Open a command prompt and execute the command:
log show --predicate 'subsystem == "com.apple.eapol"'Attempt to connect to the WiFi access point.
Examine the log, which will product results similar to:
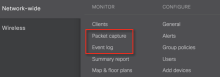
2019-04-10 15:38:53.868667-0400 0x1caacd Default 0x0 17296 0 eapolclient: [com.apple.eapol:Client] en0 START uid 501 gid 20 2019-04-10 15:38:54.062713-0400 0x1caacd Default 0x0 17296 0 eapolclient: [com.apple.eapol:Client] en0: 802.1X User Mode 2019-04-10 15:39:02.510875-0400 0x1caacd Default 0x0 17296 0 eapolclient: [com.apple.eapol:Client] en0 EAP-TTLS: successfully authenticated 2019-04-10 15:39:11.117972-0400 0x1caacd Default 0x0 17296 0 eapolclient: [com.apple.eapol:Client] en0 STOP - On Meraki cloud admin dashboard, navigate to Network-wide, and select either Packet capture or Event Log, as shown below.
Interpreting Wireshark captures
At a high level, there are three stages in the communication between the supplicant/AP and the RADIUS server when an authentication takes place:
- exchange of EAP-Identity and EAP-Start messages
- TLS Handshake, starting with a ClientHello
- RADIUS Access-Accept, followed by a 4-way EAPoL handshake between the AP and supplicant