Test the Fortinet appliance integration
There are two tests to verify the Fortinet SSL VPN Appliance is properly configured to work with Okta.
- Network Flow Diagram
- Test SSL-VPN with Fortinet
- Test the clientless VPN with the Fortinet web portal
Network Flow Diagram
Test SSL-VPN with Fortinet
-
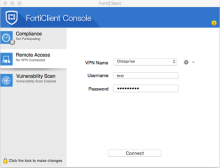
Open the Fortinet app and select Remote Access, as shown below.
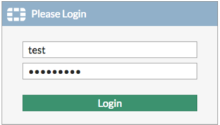
- Enter your Username and a Password.
- The username must be in the format you specified when you added the app in Okta in Part 2, above.
- If configured, you concatenate the Password with a one-time password (OTP) or a keyword; for example Password1,123456, Password1,push, or Password1,sms, as detailed below.
- 123456 – code from Okta Verify, Google Authenticator, or Yubikey OTP
- push – trigger push notice to enrolled phone
- sms – trigger sms to enrolled phone
- other – any other configuration
- Click Connect.
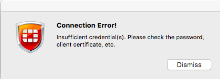
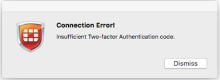
- If the Connection Error! dialog is displayed, check your username and password and try again.
-
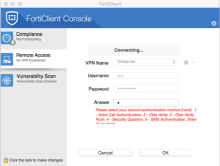
When the challenge screen appears, enter the number that corresponds with the appropriate second factor and click Continue. Follow the prompts to enter the second factor challenge and then, click OK. Users are challenged for a second factor to use based on the devices they have enrolled.
-
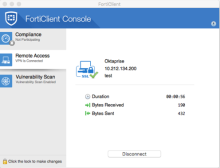
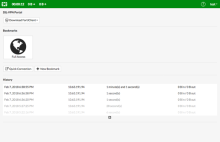
After successfully completing the challenge, you are connected.
The FortiClient Console displays the connection details.
If you enter an incorrect value or take too long to respond to the push notification, the Connection Error! dialog is displayed.
Test the clientless VPN with the Fortinet web portal
- Navigate to the Fortinet web portal URL.
- Enter your Username and Password.
- The username must be in the format you specified when you added the app in Okta in Part 2, above.
- If configured, you concatenate the Password with a one-time password (OTP) or a keyword; for example Password1,123456, Password1,push, or Password1,sms, as detailed below.
- 123456 – code from Okta Verify, Google Authenticator, or Yubikey OTP
- push – trigger push notice to enrolled phone
- sms – trigger sms to enrolled phone
- other – any other configuration
- Click Connect.
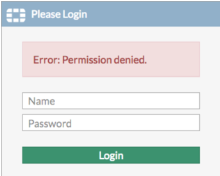
- If you receive the Login Failed screen shown below, check your username and password and try again.
-
When the challenge screen appears, enter the number that corresponds to the appropriate second factor. Follow the prompts to enter the second factor challenge and then, click Login. Users are challenged for a second factor to use based on the devices they have enrolled.
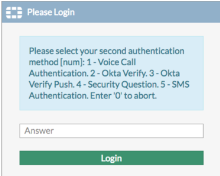
-
After successfully completing the challenge, you are connected and see the screen shown below.
If you enter an incorrect value or take too long to respond to the push notification, the following dialog is displayed: