Okta Classic Engine release notes (Preview)
Version: 2024.05.0
May 2024
Generally Available
Option to enforce profile source priority for Desktop Single Sign On
Enforcing profile source priority for DSSO requires end users to authenticate using their identity from the top prioritized profile source. See Delegated authentication.
Microsoft Graph commands for Office 365 Manual Domain Federation
The Manual Domain Federation configuration guide for Microsoft Office 365 now uses Microsoft Graph commands.
Sign in with duplicated email authenticators
Previously, users couldn’t sign in if they had the same email enrolled twice as an authenticator. This change checks the status of each email authenticator and allows the user to sign in with the most suitable email authenticator.
OIN connector support for Entitlement Management
The GitHub Team connector has been updated to support Entitlement Management. See Provisioning-enabled apps.
System Log events for Workflows execution history
Three new event types have been added to the System Log for logging Workflows execution history events:
- workflows.user.flow.execution_history.activate
- workflows.user.flow.execution_history.deactivate
- workflows.user.flow.execution_history.delete
See the Event Types API.
System Log event updates for sign-on policies
The following System Log events are updated to include more debug data and change details about added, updated or deleted rules:
- application.policy.sign_on.rule.create
- application.policy.sign_on.rule.delete
- application.policy.sign_on.update
- policy.lifecycle.update
- policy.rule.update
System Log event update for Trusted Origins
If a Trusted Origin is updated using an Event Hook, the event hook ID is now displayed in the System Log event.
Early Access
Skip the verify page and redirect to the IdP authenticator
This feature allows users to skip the verify step in the Sign-In Widget. They are instead redirected to the IdP authenticator for verification. When you enable this feature, end users see the option to skip the Sign-In Widget verification. If your org is configured to remember the last authenticator the user used, then the user is auto-redirected to the IdP authenticator for future sign-in attempts.
Require MFA for Admin Console access
You can require multifactor authentication to access the Okta Admin Console. When you enable this feature, all Admin Console authentication policy rules that allow single factor access are updated to require multifactor authentication. See Enable MFA for the Admin Console.
Fixes
-
Failed Group Push operations to ServiceNow weren't displayed on the Tasks page. (OKTA-677484)
-
Provisioning to UKG Pro sometimes failed due to WorkCountryCode. (OKTA-681623)
-
An internal error caused IWA agent upgrades to fail. (OKTA-693810)
-
Performing a Push Now operation on an empty push group in Okta failed to reconcile the group in Zendesk. (OKTA-701099)
-
Stuck XaaS executions weren't marked as failed jobs. (OKTA-712091)
-
Users who entered an invalid username into a password-first sign-in flow saw a misleading error message. This behavior occurred only in orgs that enabled the Multiple Identifiers feature and disabled User Enumeration Prevention. (OKTA-713096)
-
When Okta detected a change in an admin’s IP, the caep_session_revoked signal wasn't sent to the SSF receiver. This occurred when the IP binding for admin console setting was enabled. (OKTA-717305)
-
Active Directory incremental imports were converted to full imports when a new OrganizationUnit was added or an existing OrganizationUnit was renamed. (OKTA-718186)
-
Super admins with roles assigned through group assignment couldn't enable Direct Authentication grant types in an OIDC app. (OKTA-719756)
-
When running delegated flows from the Okta Admin Console, the event metadata wasn't recorded by the System Log. (OKTA-722302)
-
Smart Card IdP username transformation didn't allow the space characters within the username string. This functionality is only available with custom UD attributes. (OKTA-723152)
-
The Edit button for modifying an SSWS API token's rate limit was disabled instead of hidden for admins who didn't have permission to update the rate limit. (OKTA-724333)
Okta Integration Network
- DigiCert (SWA) was updated. (OKTA-722381)
- Foqal Agent (SAML) is now available. Learn more.
- Kantega SSO (OIDC) is now available. Learn more.
- Kantega SSO (SAML) is now available. Learn more.
- Kantega SSO (SCIM) is now available. Learn more.
- LimbleCMMS (OIDC) now has additional redirect URIs.
- Netdata (OIDC) is now available. Learn more.
- Obsidian Security (SAML) now has an option to select the region for the ACS URL.
- SCIM 1.1 Test App (OAuth Bearer Token) now has SWA and SAML functionality.
- SCIM 2.0 Test App (OAuth Bearer Token) now has SWA and SAML functionality.
- SCIM 2.0 with Entitlements Management (Basic Auth) now has SWA and SAML functionality.
- SCIM 2.0 with Entitlements Management (Header Auth) now has SWA and SAML functionality.
- SCIM 2.0 with Entitlements Management (OAuth Header Auth) now has SWA and SAML functionality.
- Vansec (SCIM) now has updated application profile and mappings.
Weekly Updates
Fixes
-
Inactive app users weren't included in group pushes for AWS Account Federation. (OKTA-678930)
-
Workday imports intermittently fail due to connection resets. (OKTA-696604)
-
Groups IDs were sent as part of PATCH operations. (OKTA-711633)
-
When ADSSO routing was enabled for an org, users of impacted app instances couldn't reach the sign-in page after clicking an OAuth 2.0 device activation link. (OKTA-724269)
-
The logOnly attribute incorrectly appeared in the System Log. (OKTA-725287)
-
Sometimes actions that were taken on role assignments from entitlement bundles timed out. (OKTA-727294)
-
Orgs that had Auto-enroll in all future EA features enabled in Features didn't get the Enforce MFA For Admin Console feature. (OKTA-729278)
Okta Integration Network
- Amazon WorkDocs by Aquera (SCIM) description was updated.
- Amazon WorkMail by Aquera (SCIM) description was updated.
- Asana (SWA) was updated. (OKTA-721354)
- Codefresh by Aquera (SCIM) description was updated.
- Costimize (OIDC) is now available. Learn more.
- Genian NAC (SAML) is now available. Learn more.
- Grafana by Tech Prescient (SCIM) is now available. Learn more.
- Highway (OIDC) is now available. Learn more.
- JazzHR by Aquera (SCIM) is now available. Learn more.
- NinjaOne (SAML) is now available. Learn more.
- NordLayer (SCIM) description was updated.
- Nudge Security (OIDC) description was updated.
- Pando HR (OIDC) is now available. Learn more.
- ProdPad by Aquera (SCIM) description was updated.
- Proton VPN (SAML) is now available. Learn more.
- Smartsheet SCIM (SAML) was updated to remove ACS URL and audience requirements.
- SwaggerHub by Aquera (SCIM) description was updated.
- TriNet by Aquera (SCIM) description was updated.
Okta Personal for Workforce
Okta Personal for Workforce is a set of features that allows admins to separate their users' work data from non-work data. Admins can now offer their end users a free Okta Personal account to store personal data, allow them to switch between accounts, and migrate personal apps from Okta enterprise tenant to Okta Personal. When Okta Personal for Workforce is enabled, personalized comms will be sent to the end users encouraging them to use Okta Personal for personal data and Okta enterprise for work data. See Okta Personal for Workforce User Experience.
Content security policy enforcement on end-user pages
Content Security Policy is now enforced for end-user pages in orgs with custom domains. Content Security Policy headers help detect attacks such as cross-site scripting and data injection by ensuring browsers know what kind of actions the webpage can execute. Future iterations of the Content Security Policy enforcement for end-user pages will become stricter than this first release. This feature will be gradually made available to all orgs.
Okta ThreatInsight coverage on core Okta API endpoints
Okta ThreatInsight coverage is now available for core Okta API endpoints (OpenID Connect & OAuth 2.0, Okta Management, and MyAccount API). Based on heuristics and machine learning models, Okta ThreatInsight maintains an evolving list of IP addresses that consistently show malicious activity across Okta's customer base. Requests from these bad IP addresses can be blocked or elevated for further analysis when Okta ThreatInsight is enabled for an Okta org.
Previously, Okta ThreatInsight coverage only applied to Okta authentication endpoints (including enrollment and recovery endpoints). With this release, enhanced attack patterns are detected for authentication endpoints and limited attack patterns are also detected for non-authentication endpoints.
There are no changes to the existing Okta ThreatInsight configuration. You can still enable Okta ThreatInsight with log and block mode, log mode, and exempt network zones. A new Negative IP Reputation reason is available for high security.threat.detected events. See System Log events for Okta ThreatInsight.
Application Entitlement Policy
Administrators can now override attribute mapping when assigning apps to individuals or groups. Attributes can also be reverted to their default mappings. See Override application attribute mapping. This feature will be gradually made available to all orgs.
Descriptive System Log events
When Okta identifies a security threat, the resulting security.threat.detected entry now provides a descriptive reason for the event. See System Log.
New App Drawer
The updated app settings panel on the Okta End-User Dashboard allows end users to see all app details in a single view without having to expand multiple sections. End users can quickly differentiate between SWA apps where they have set a username and password and SAML / OIDC apps that are admin-managed with no additional user settings. The updated app settings panel also provides accessibility improvements with better screen reader support and color contrast. See View the app settings page.
SSO apps dashboard widget
The new SSO apps widget displays the number of user sign-in events across each of your org’s apps over a selected period of time. You can use it to see which apps are used most frequently and to easily monitor the authentication activity across your org. See Monitor your apps.
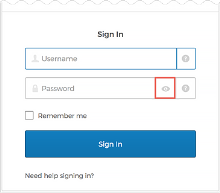
Toggle password visibility on the Okta Sign-In page
End users can now toggle visibility of their password on the Sign-In Widget, allowing them to check their password before they click Sign In. Note that passwords are visible for 30 seconds and then hidden automatically. See Authentication. See Delegated authentication.
Email failure events in the System Log
Admins can now view email delivery failure events in the System Log. This helps admins better monitor the email event activity in their org. See System Log.
Federation Broker Mode
The new Federation Broker Mode allows Okta SSO without the need to pre-assign apps to specific users. Access is managed only by the authentication policy and the authorization rules of each app. This mode can improve import performance and can be helpful for larger-scale orgs that manage many users and apps. See Manage Federation Broker Mode.
User Import Scheduling
When importing users from an app to Okta, you can now schedule imports to occur at hourly, daily, or weekly intervals. Scheduling imports at a time that is convenient for your org reduces the likelihood of service disruptions and eliminates the need to start imports manually. If an application allows incremental imports, you can create both full and incremental import schedules. This is a self-service feature. See Edit app provisioning settings.
Choose additional filters for Office 365 sign-on policy
Filters have been added to enable admins to distinguish between web browsers and Modern Authentication clients when creating an app sign-on policy. See Office 365 sign-on rules options.
Device Authorization grant type
Advancements in internet technology have seen an explosion of smart devices and the Internet of Things. Consumers need to sign in to applications that run on these devices, but the devices either lack support for a web browser or have limited ability for input, such as smart TVs, car consoles, and thermostats. As a result, users resort to insecure authentication solutions that are error-prone and time-consuming.
The Device Authorization grant feature is an OAuth 2.0 grant type that allows users to sign in to input-constrained devices and also to devices that lack web browsers. This feature enables users to use a secondary device, such as a laptop or mobile phone, to complete sign-in to applications that run on such devices. See Configure Device Authorization.
Null values for SCIM provisioning
Null values for any attribute type can now be submitted to Okta when using SCIM provisioning. This change reduces the error messages customers receive and simplifies end user identity management. See Manage profiles.
Manage admin email notification subscriptions using API endpoints
Admins can manage email subscriptions using the Admin Email Subscription API endpoints.
-
Super admins can configure default subscription settings by admin type.
-
All admins can manage their own admin email notification subscriptions.
End-User Dashboard and Plugin redesign
The Okta End-User Dashboard and Okta Browser Plugin have been redesigned with a modern look and feel that includes new sidebar navigation, fuzzy search, and sections that replaces tabs.


Admins can enable this new design all at once or by groups. The new experience is 50% faster, more intuitive to use, and more responsive to smaller screens. Design changes also improve accessibility and app discovery for end users.
See Create sign-on policies with Okta Applications.
This feature will gradually be made available to all Preview orgs.
LDAP password reset option
LDAP delegated authentication settings can now be configured to allow users to reset their passwords. This change reduces the time needed for password management and allows users to reset their passwords quickly and easily. See Delegated authentication.
LDAP admin password reset
For orgs integrated with LDAP, admins can now perform password resets for an active individual end user. See Reset a user password.
Windows Device Registration Task, version 1.4.1
This release fixed the following issues:
- If there was a space in the sAMAccountName, an error appeared when installing the Okta Device Registration task and the installation completed but didn't function.
- An unknown publisher warning appeared after double-clicking the Okta Device Registration MSI file.
Affected customers should uninstall the registration task and install 1.4.1 or later.
See Enforce Okta Device Trust for managed Windows computers and Device Trust for Windows Desktop Registration Task Version History.
Incremental Imports for CSV
Incremental imports improve performance by importing only users who were created, updated, or deleted since your last import. See Manage your CSV directory integration. Note that this feature is being re-released having previously been released to Production in 2020.09.0.
Password changed notification email
To eliminate unnecessary email notifications, the Password changed notification email setting is no longer enabled by default on new preview orgs. See Password changed notification for end users.
Office 365 Silent Activation
Using Okta as the Identity Provider, Okta Office 365 Silent Activation allows for a seamless experience for your Microsoft Office 365 end users accessing Office 365 apps on domain joined shared Workstations or VDI environments. Once your end users have logged into a domain-joined Windows machine, no further activation steps are required. See Office 365 Silent Activation: New Implementations.
End-user Welcome emails localized
The ability to localize the Welcome email that Okta sends to new end users by referencing the users' default locale property is now Generally Available. See Configure general customization settings.
People page improvements
The People page has been improved so the people list can be filtered by user type. See Universal Directory custom user types known issues.
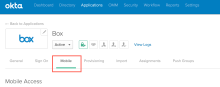
Mobile tab available for mobile-capable apps
The Mobile tab available in the Okta Admin Console for mobile-capable OIN apps allows you to publish mobile applications to an App Store and deploy them to your end users.
Provisioning page UI element change
Drop-down menus on the Provisioning page (General Settings) were standardized.
UI element change
Drop-down menus on the Provisioning page (General Settings) are standardized. See Provision applications.
Early Access features, auto-enroll
You can now opt to auto-enroll in all Early Access features, instead of having to enable them as they become available.
Connecting Apps to Okta using the LDAP Interface
The LDAP Interface allows you to authenticate legacy LDAP apps to Universal Directory in the cloud. With the LDAP Interface, authentication is done directly against Okta via LDAP, without the need for an on-premise LDAP server. In addition, the LDAP interface supports other LDAP functions like search. See Set up and manage the LDAP Interface.