Amazon Web Services (AWS) integration
This topic describes the steps to integrate Identity Security Posture Management (ISPM) with your Amazon Web Services (AWS) organization.
The steps require you to create a read-only role using a Cloud Formation Stack for the management accounts. You also need to create a read-only role using a Cloud Formation StackSet for the member accounts. While integrating AWS with ISPM, it's important that you include the External ID for the stack and stackset. The role you create allows ISPM access to the following things:
-
Configuration & Resource Metadata
-
AWS IAM Identity Center and Directory Service settings
-
CloudTrail logs
Before you begin
-
You must have access to your AWS management account. To verify that you're signed in to the management account, perform the following steps:
-
Sign in to your AWS account.
-
Click your account name.
-
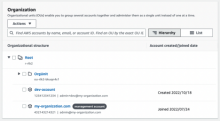
Select Organization.
If you're in the management account, you can view the organization's hierarchy.
-
-
In the Identity Security Posture Management console, go to .
Create an IAM role in the management account
-
Go to the AWS console of your management account and search for CloudFormation.
-
Select Stacks.
-
Click Create stack and select With new resources (standard) from the dropdown menu.
-
In the Prerequisite - Prepare template section, select Template is ready.
-
In the Specify template section, select Amazon S3 URL as the template source.
-
Enter this URL: https://spera-prod-public.s3.us-west-1.amazonaws.com/integrations/aws/spera-prod-cloud-formation-0429d3.json
-
Click Next.
-
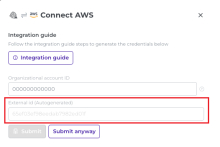
On the Specify stack details page, enter the stack name (for example, OktaISPMstack) and the external ID that you copied from the ISPM console earlier.
-
Click Next.
-
Scroll to the end of the Configure stack options page, and then click Next.
-
Review the details on the page.
-
Scroll to the end of the page, and then select the I acknowledge that AWS CloudFormation might create IAM resources with custom names checkbox.
-
Click Submit.
-
Go back to .
-
Check the status of your stack. You may have to wait for AWS to execute the stack. If the execution was successful, the status appears as CREATE_COMPLETE.
Create IAM roles in all member accounts
-
Go to the AWS console and search for CloudFormation.
-
Select StackSets.
-
Optional. If a notification for enabling trusted access appears, click Enable trusted access.
-
Click Create StackSet.
-
In the Permissions section, select Service-managed permissions.
-
In the Specify template section, select Amazon S3 URL as the template source.
-
Enter this URL: https://spera-prod-public.s3.us-west-1.amazonaws.com/integrations/aws/spera-prod-cloud-formation-0429d3.json
-
Click Next.
-
Enter the following information:
-
The name of the stack and that you created while creating an IAM role in the management account. For example, OktaISPMstack.
-
The external ID you copied earlier from the ISPM console.
-
-
Click Next.
-
In the Execution configuration section, select Inactive and click Next.
-
In the Deployment targets section, select Deploy to organization.
-
Go to , select Enabled.
-
In the Specify regions section, select US East (N. Virginia).
-
Click Next.
-
Review the details on the page.
-
Scroll to the end of the page and select the I acknowledge that AWS CloudFormation might create IAM resources with custom names checkbox.
-
Click Submit. If the execution is successful, the status appears as SUCCEEDED.
Don't delete the Stack and the StackSet when you finish these steps. You need resources that were generated for the integration.
Share the parameters with ISPM
- Ensure that you're signed in to the management account.
- Click your organization name to view the account ID.
-
In the Identity Security Posture Management console, go to .
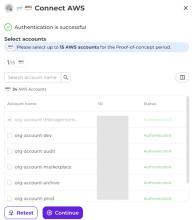
- Select Amazon Web Services.
- Enter the Account ID.
- Click Submit.
- Select the accounts (tenants) that ISPM should monitor.
- Click Continue.