Configure Single Sign-On for Microsoft Entra ID
Configure Single Sign-On (SSO) access from your Microsoft Entra ID (formerly known as Azure Active Directory) tenant to Identity Security Posture Management (ISPM) using a Microsoft Entra ID enterprise app integration. To do this, there are several tasks that you need to complete:
Copy your tenant name
- Sign in to the Microsoft Azure portal using an account that has permission to manage apps.
- If you have access to multiple tenants, go to to select the tenant where you want to register the ISPM app.
- Copy your Tenant name and store it safely.
Register ISPM in Microsoft Entra ID
-
In the Microsoft Azure portal, search for and select Microsoft Entra ID.
-
Click Add, and then select App registration.
-
Enter a name for your app, for example ISPM Login.
-
Set Supported account types as Accounts in this organizational directory only. If you have a multi-tenant AAD, select Accounts in any organizational directory.
-
Select Web as the Redirect URI, and enter https://spera.us.auth0.com/login/callback as the callback URL.
-
Click Register.
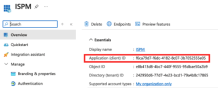
Copy the application ID
Copy the client secret
- Go to .
- Click New client secret:
- Enter a description.
- Select 24 months as the expiration.
- Click Add
- Copy the Value and store it safely.
This value isn't displayed again and can't be retrieved by other means. It's referred to as the client secret going forward.
Configure your app
- In the Microsoft Azure portal, search for and select Microsoft Entra ID.
- Go to .
- Search and select the app that you registered.
- Go to .
- Set Assignment required? to Yes to only allow users who are assigned to the app to access it.
- From the left menu, select Users and groups and assign users or groups to allow them to access the app. See Microsoft help.
Share the parameters with ISPM
- In the Identity Security Posture Management console, go to .
- Select Configure AAD SSO.
- Enter the following information:
- Tenant name (the tenant primary domain
- Application (client) ID
- Client secret
- Click Submit.