Identity Security Posture Management overview
Okta Identity Security Posture Management helps you take control of identity and access sprawl in your organization by uncovering hidden risks, prioritizing critical threats, and guiding remediation.
Identity Security Posture Management is generally available on a subscription basis in North America. Contact your Account Executive or Customer Success Manager.
Problem
Malicious actors exploiting users (both human and machine) to gain unauthorized access to organization infrastructure is a common threat across organizations. It's also difficult for security teams to verify if security controls are implemented properly because they lack deep visibility and risk analysis in the complex Cloud and SaaS environments.
The solution
Use Identity Security Posture Management to proactively reduce the identity attack surface and improve the security of your organization:
-
Uncover hidden threats and misconfiguration across identity providers, SaaS, and Cloud infrastructure (IaaS).
-
Discover and prioritize vulnerabilities like MFA bypass, overprovisioned users with elevated accumulated permissions, and improper offboarding. See Supported detections.
-
Enable ongoing risk-based monitoring against security, IAM, and compliance standards (such as NIST, CIS, ISO, SOX, and PCI-DSS).
-
Gain actionable security insights to drive quick remediation.
-
Get ongoing, continuous analysis of your identity security exposure within minutes with rapid deployments.
With the information that Identity Security Posture Management provides, you can handle these use cases:
-
Enforce Least Privilege and Zero Trust Access frameworks
Identity Security Posture Management provides prioritized and usage-based recommendations about the utilization of identities, permissions, and groups. You can use these to drive effective remediation.
-
Increase the efficiency and productivity of security and IT teams
Identity Security Posture Management provides consolidated context across systems and people. It also allows you to export reports, filter the insights and data by segments like users and service accounts, users with specific roles, groups, and apps. It helps you simplify complex systems by giving you a graphical representation of the system.
How it works
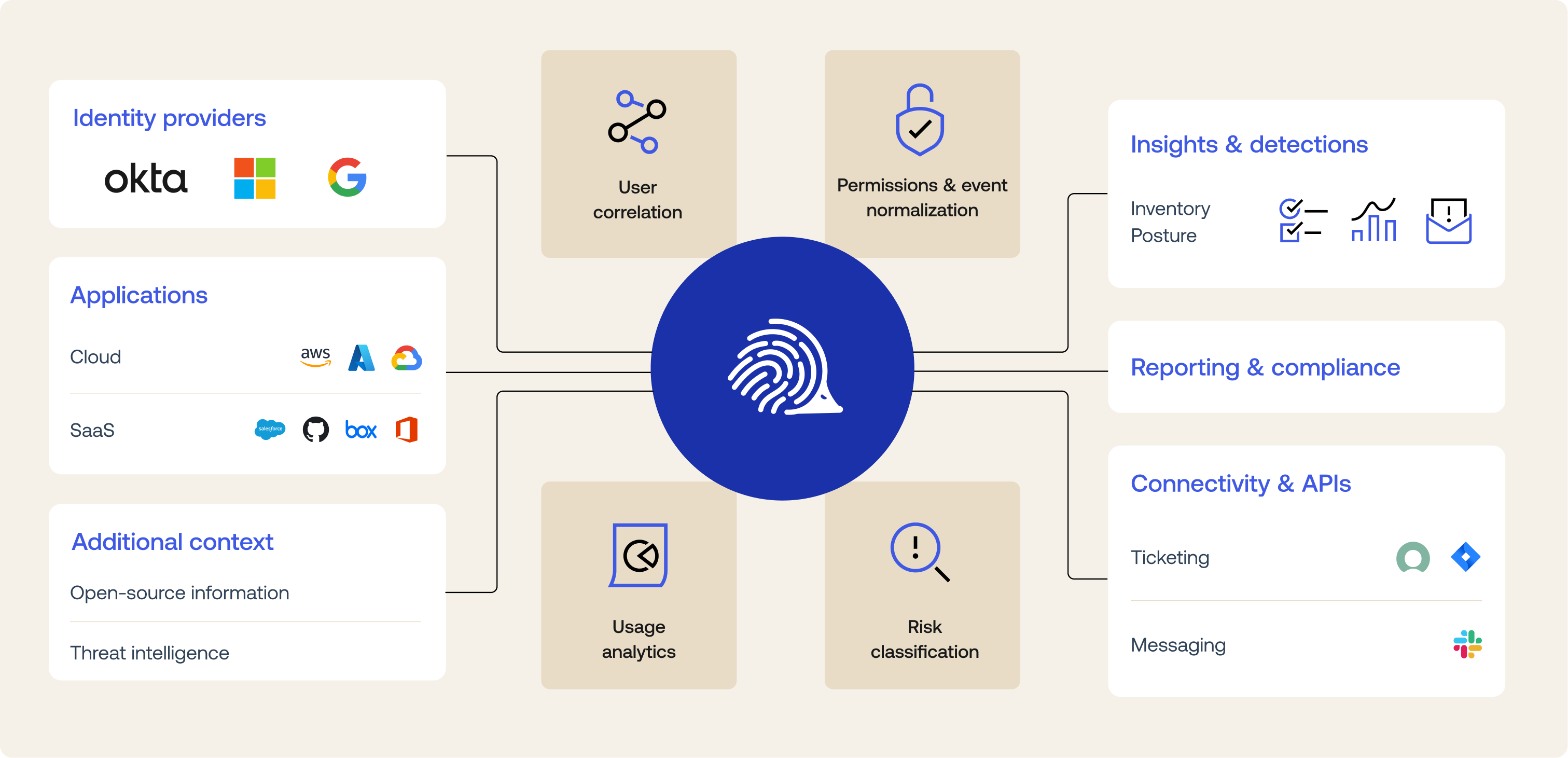
Identity Security Posture Management uses an agentless process to integrate quickly and seamlessly with your identity providers, SaaS applications and Cloud infrastructure to provide continuous visibility into identities, permissions, and actions.
It normalizes and contextualizes data, performs risk classification on the usage analysis, and prioritizes identity issues based on attack chains and consolidated context. Using graphical visualization and reporting capabilities, the centralized platform helps you instantly understand the biggest gaps and risks in your organization.
You can also integrate Identity Security Posture Management to your organization's workflows such as ticketing and messaging systems.
The information, risk level, priority, or recommendations that Identity Security Posture Management provides to reduce the identity attack surface of your organization isn't legal, security, or compliance advice. Learn more.
