Create the app in Access Gateway
During this task we will create the JD Edwards application, specify a certificate (if required) and then add the required redirect policy.
Topics:
- Create application
- Configure the application
- [Optionally] Configure load balancing
- [Optionally] Configure certificates
- Configure policy
Create application
To create the application in Access Gateway:
- Sign in to the Access Gateway Admin UI console.
- Click the Applications tab.
- Click +Add.
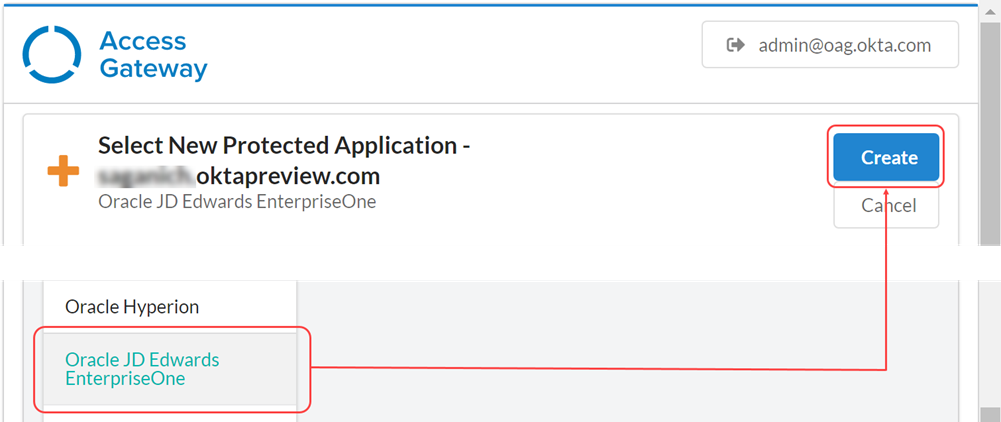
-
From the Application menu, select Oracle JD Edwards Enterprise One, and click Create.
See the Supported technologiessection in Supported technologies.
Configure the application
In the Essentials pane enter:
| Field | Value |
|---|---|
| Label | The name of the application, For example: JD Edwards |
| Public Domain | The external facing URL of the application. For example: https://jde-external.example.com |
| Protected Web Resource | The URL and port combination of the Oracle JD Edwards Implementation that is being protected. For example: http://jde-internal.example.com:7005 See Configure load balancing |
| Post Login URL |
Enter an appropriate target URL. Post Login URL may contain other elements specific to the implementation. |
| Group | The group containing users who can access the JD Edwards instance. |
Configure load balancing
Only use Access Gateway as the load balancer. See Load balancing.
- Expand the Protected Web Resource tab.
- Enable Load Balancing By Access Gateway. A table of hostnames and weights representing the target load-balancing instances appears. This table is initially empty. Click the Edit
 icon to modify an entry in the table, or click the Delete
icon to modify an entry in the table, or click the Delete  icon to delete an entry.
icon to delete an entry. - Choose either HTTP or HTTPS as the URL scheme. Each protected web resource that you add inherits this scheme.
- Optional. Enable and enter the Host Header value.
- Complete the following steps to add a host. Repeat these steps as required:
- Click Add protected web resource.
- Enter a fully qualified hostname:port combination, like for example, https://backendserver1.atko.com:7001.
- Enter a weight from 1 to 100. Enter 0 to specify that a host is disabled.
Weights represent the percentage of requests that are routed to this host. For example, two hosts of weights 2:1 result in requests being routed approximately 66% to the host weighted 2 and approximately 33% to the host weighted 1.
- Click Okay.
-
Optional. Configure health checks. They use GET operations to confirm that back-end resources are functional. New requests aren't routed to resources that have been labeled unhealthy by the health checks.
- Enable Load Balancer Health Check.
- Click Edit to modify health check settings.
- Modify the settings as required.
Field Value Default
Path The URI path to the resource used in the health check. / Method The HTTP method used in the health check. Always GET Status code The HTTP status code used to determine health. 200 Interval The interval between health checks in seconds. 10 Request timeout The health check request timeout in seconds. 1 Healthy threshold The number of requests that must succeed before a host is considered healthy. 3 Unhealthy threshold The number of requests that must fail before a host is considered unhealthy. 3 - Click Save.
Configure certificates
All apps, including the Access Gateway Admin UI console app, require a self-signed or signed certificate.
Include signed certificates wherever you terminate SSL. You can terminate SSL at Access Gateway or any other network component, like a load balancer.
If you terminate SSL at a load balancer, on the Access Gateway Admin UI console app, you also need to use a certificate that is trusted by the load balancer.
If you terminate SSL on the Access Gateway Admin UI console application, you must use a signed certificate, which must be on the Access Gateway node and be associated with the Access Gateway Admin UI console application.
- See Certificate use for details about certificates.
- See Certificate management for a task flow for obtaining and assigning certificates.
- Expand the Certificates tab.
By default, when you create the app, the system generates a self-signed wildcard certificate and assigns it to the app.
- Optional. Click Generate self-signed certificate. A self-signed certificate is created and automatically assigned to the app.
- Optional. Select an existing certificate from the list. Use the Search field to narrow the set of certificates by common name. Use the page forward and backward arrows to navigate through the list.
-
Click Next. The Attributes pane appears.
For detailed information on the attribute options, see App attributes .
- Confirm the IDP login attribute.
By default the JD Edwards application template login field as the JDE_SSO_UID header. Change the value of the header field if required. Add additional header fields required by the application.
Configure policy
-
Click Next. The Policies pane displays.
- On the root policy row, click the Edit icon
 .
. - Expand the Advanced sub-tab.
- In the Custom configuration tab, enter a proxy redirect for the target JD Edwards application.
For example:
proxy_redirect http://jde-app.domain.tld:7005 https://$host:$server_port; - Click Not validated when complete.

If all values are entered correctly, the Not Validated button will change to Validated.
- Click Okay.
- Click Done.
