Configure log forwarders
Access Gateway enables you to use log forwarders to store your log files in third-party log products.
Before you begin
- Verify that a third-party log product has already been set up and can receive events from Access Gateway.
- Use this connection information for the third-party log product:
Parameter
Example
A fully qualified IP address or DNS-resolvable name of the third-party log product 192.168.1.1
my.logproduct.server
Protocol TCP or UDP Listen port
Access Gateway validates the logging server connection. Verify that this port is open before you forward logs from Access Gateway to the third-party log product.
5514 - In high availability clusters, when you add a log forwarder definition to the main admin node, the definition propagates to all worker nodes. Worker nodes then send log events directly to the third-party log product server.
Create a log forwarder receiver
You must create a location that receives log data from Access Gateway. Your log product might call this a receiver, an input, a listener, a remote listener, or a log forwarder receiver.
See that product's documentation for instructions.
Add a log forwarder in Access Gateway
- In your Access Gateway instance, select Backups and Logs and Backups.
- Select Log Forwarder.
- Click .
- Configure the following options:
- Name: Enter a name for the forwarder.
- Feed: Select one of these options:
- AUDIT: Log entries representing user authentication.
- ACCESS: Log entries for user authorization and app accesses.
- MONITOR: Log entries for app configuration (add, delete, modify), certificate configuration, and Auth Module configuration.
- ACCESS, AUDIT & MONITOR: All of these sources.
AGGREGATE: Sends log entries for AUDIT, ACCESS, MONITOR, services, Secure Shell (SSH) sessions, sudo access, the Access Gateway Admin UI console, and EBS agent logs.
The ACCESS, AUDIT & MONITOR and AGGREGATE feeds are available in Access Gateway 2025.6.0 and higher.
- Protocol: Select UDP or TCP. This protocol must be the same as the protocol you selected for communication with your third-party logging product.
- Host: The DNS-resolvable hostname or IP address of the third-party log product.
- Port: The port that you're using to communicate with the third-party log product.
- Click Validate Forwarder. Access Gateway attempts to validate the connection information for the third-party log product. Correct any input errors if they appear. When the connection has been validated, the Validate Forwarder button changes to Forwarder Validated.
- Click Okay.
- The log forwarder definition appears in the list of log forwarders. Its initial status is Testing, which changes to Valid when it passes testing.
Test log forwarders
After you've configured a receiver for your log events and created a log forwarder in Access Gateway, you can test that everything works as expected.
- Configure a system logger in your log server.
- Configure a log forwarder in Access Gateway. For testing purposes, Okta recommends that you use ACCESS mode. This mode records sign-in events to the Access Gateway Admin UI console.
- Verify that your third-party log product is started and is ready to receive events.
- Sign out of and then back into the Access Gateway Admin Console.
- Verify that these events appear in the third-party log product feed. See the Feed examples section for examples.
Feed examples
| Type | Description |
|---|---|
| AUDIT | Audit log events include log entries representing user authentication. See Access Gateway audit log for details and examples of audit events. Sample events: 2020-06-24T10:05:56.000-05:00 example.myaccessgateway.com ACCESS_GATEWAY WEB_CONSOLE - - INFO SYSTEM_STARTUP [] Startup complete, system ready.2020-06-24T04:00:01.000-05:00 example.myaccessgateway.com ACCESS_GATEWAY WEB_CONSOLE IDP LOCAL INFO SYSTEM_IDP_STATUS [NAME="MyIDP" DOMAIN="someorg.oktapreview.com" TYPE="IDP_OKTA" RESULT="PASS" REASON="VALID"] Success confirming IDP status with: someorg.oktapreview.com. |
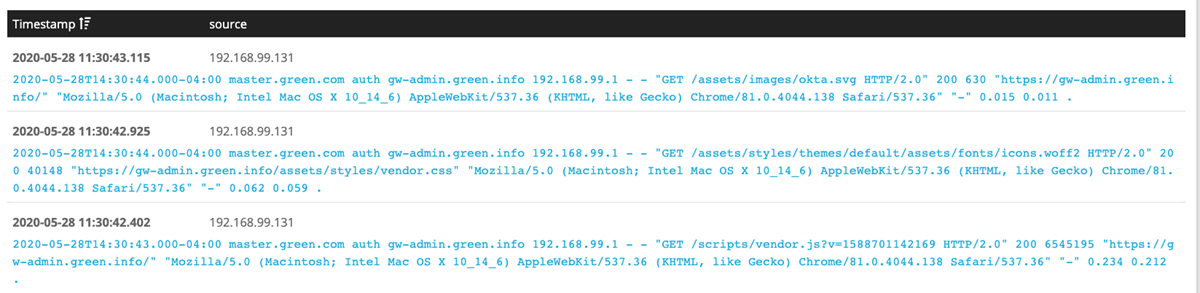
| ACCESS | Access log events include log entries representing user authorization and app accesses. For example, a particular user accessed a particular app from a given IP address. See Access Gateway access log for details and examples of access events.
Sample event: 2020-06-24T09:41:08.000-05:00 example.myaccessgateway.com auth header.myexample.com 10.0.0.110 - - "GET /assets/images/image.png HTTP/2.0" 200 1229 "https://gw-admin.example.com/" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36" "-" 0.029 0.028 . |
| MONITOR | Monitor log events include log entries representing app configuration (add, delete, modify), certificate configuration, and Auth Module configuration. See Access Gateway monitor log Sample event: 2020-06-25T07:00:02.119-05:00 example.myaccessgateway.com OAG_MONITOR MONITOR DISK_USAGE INFO DISK_USAGE [FILESYSTEM="/dev/mapper/centos-root" MOUNT="/" USAGE="12%"] Mount / is 12% full |
|
AGGREGATE |
2025-06-04T21:21:19.000+00:00 example.myaccessgateway.com ACCESS_GATEWAY EBS_SSOAGENT Commencing graceful shutdown. Waiting for active requests to complete 2025-06-04T21:21:20.000+00:00 example.myaccessgateway.com ACCESS_GATEWAY EBS_SSOAGENT Graceful shutdown complete . 2025-06-04T21:21:52.875+00:00 example.myaccessgateway.com systemd Stopped EBS SSO Agent. 2025-06-04T21:21:52.875+00:00 example.myaccessgateway.com systemd Starting EBS SSO Agent... . . 2025-06-04T21:21:52.995+00:00 example.myaccessgateway.com systemd Stopping Access Gateway Web Console... 2025-06-04T21:21:55.000+00:00 example.myaccessgateway.com ACCESS_GATEWAY WEB_CONSOLE Commencing graceful shutdown. Waiting for active requests to complete 2025-06-04T21:21:55.000+00:00 example.myaccessgateway.com ACCESS_GATEWAY WEB_CONSOLE Graceful shutdown complete . . 2025-06-04T21:22:00.889+00:00 example.myaccessgateway.com systemd Stopped Access Gateway Web Console. 2025-06-04T21:22:00.890+00:00 example.myaccessgateway.com systemd Starting Access Gateway Web Console... . 2025-06-04T21:49:54.978+00:00 example.myaccessgateway.com sshd Accepted password for oag-mgmt from x.x.x.x port xxxxx ssh2 |