Protected Rule resource-matching rule expressions
Protected Policy rules require a resource matching rule to determine if an end user matches a rule. Resource matching rules are based on regular expressions.
Access Gateway provides a set of menu items with common baseline expressions that can be selected and modified to meet a specific need.
Modify a protected rule based on a provided expression
- Go to the Access Gateway Admin UI console.
-
Select the Applications tab.
-
Select an application that contains an existing or needs a new protected rule and click Edit.
- Select the Policies section.
- Select an existing protected rule and click Edit. Alternatively, create a new protected rule. For details of adding a new protected rule, see Manage app policies.
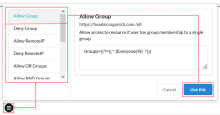
- Click the policy menu and select one of the Predefined policies, then click Use this.
- Modify the policy as required.
Predefined policies
The following predefined policies are provided:
| Policy | Description |
|---|---|
| Allow Group | Allows access to the given resource if the end user is a member of the single specified group. Example: Groups=((?=(|.:)Everyone(R|:.*))) |
| Deny Group | Denies access to the given resource if the end user is a member of the single specified group. Example: Groups=((?!(|.*:)Everyone(\R|:.*))) |
| Allow RemoteIP | Allows access to the given resource if the end users IP matches the provided regular expression. Example: RemoteIP=(?=192\..*) |
| Deny RemoteIP | Denies access to the given resource if the end users IP matches the provided regular expression. Example: RemoteIP=(?!192\..*) |
| Allow OR Groups | Allow access to resource if user has group membership to one OR another group. Example: Groups=((?=(|.*:)Everyone(\R|:.*)))|((?=(|.*:)Group2(\R|:.*))) |
| Allow AND Groups | Allow access to resource if user has group membership to one AND another group. Example: Groups=((?=(|.*:)Everyone(\R|:.*)))((?=(|.*:)Group2(\R|:.*))) |
| Allow User | Allow access to resource if UserName matches. Example: UserName=user@example.com |
| Deny User |
Deny access to resource if UserName matches. Example: UserName=(?!test@example.com) |
| Allow Group AND User | Allow access to resource if user has group membership AND UserName matches. Example: (?=.*Groups=(?=(|.:)Everyone(R|:.*)))(?=.*UserName=user1@domain.tld) |
| Allow Group AND Deny User | Allow access to resource if user has group membership AND UserName doesn't match. Example: (?=.*Groups=(?=(|.:)Everyone(R|:.*)))(?=.*UserName=(?!user3@domain.tld)) |
After being selected, the expression can be modified to meet a specific need.
Resource Matching Rule fields
Resource matching rules are regular expressions based on application attributes. Predefined polices use attributes such as Groups, UserName and RemoteIP. Any application attribute can be used in a resource matching rule. Common attribute mappings include:
| Data Source | Field | Name |
|---|---|---|
| IDP | Groups | Groups |
| IDP | UserName | |
| IDP | login | login |
| Provided and not required to be defined as attributes. | RemoteIP USER_AGENT |
|
Attributes used exclusively in resource matching rules should be Send Attribute disabled.