Okta ends browser support for TLS 1.1
Okta understands that our dependable service is integral to the important work you're doing. Ensuring the security of your environment is a top priority. Okta published a plan to align to industry best practices by making infrastructure changes to our support of Transport Layer Security (TLS) on February 13, 2018. Specifically, effective August 1, 2018, Okta only supports TLS 1.2 connections and no longer supports TLS 1.0 and 1.1 due to security vulnerabilities.
This article describes the changes that you may need to make for Microsoft Internet Explorer browsers in your organization. For TLS 1.2-related information on all Okta products and agents, and the schedule, see Migrating to TLS 1.2.
How this might affect your org
Browser versions
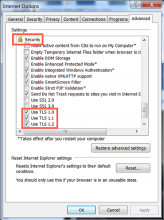
- Most vulnerable: Internet Explorer 10 is set by default to use TLS 1.1. To keep using IE 10 (and embedded browsers on systems running IE 10) with Okta, you must ensure that you configure your browsers to use TLS 1.2 (). You can use a management tool such as Group Policy Object (GPO) to update IE options on multiple workstations throughout your enterprise. For details, see Update IE on multiple workstations.
- Internet Explorer 11 is set by default to use TLS 1.2. If you change your IE 11 browsers to use TLS 1.1 or earlier, you must configure your browsers to use TLS 1.2 ().
- Clients using IE embedded browsers (such as Microsoft Office 2016 thick clients) will operate correctly on systems with IE browsers configured to use TLS 1.2. Remember, because IE 10 isn't configured with TLS 1.2 by default, an error will occur on clients with embedded IE 10 browsers unless they've been configured to use TLS 1.2.
- Edge: All versions of Edge are preconfigured to use TLS 1.2.
- Chrome, Firefox, and Safari: All recent versions of these browsers are preconfigured to use TLS 1.2.
Update Windows registry if you disabled TLS 1.2 through the registry
You must update your Windows registry only if you disabled TLS 1.2 through the registry. If this applies to workstations in your org, update the registry with the following values to ensure your end users retain access to Okta and Okta-managed apps
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server] "Enabled"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server] "DisabledByDefault"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client] "Enabled"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client] "DisabledByDefault"=dword:00000000
Update IE on multiple workstations
If appropriate for your environment, you can use a third-party management tool such as GPO to update IE options on multiple workstations throughout your enterprise.
(From a procedure entitled Disable SSL 3.0 and enable TLS 1.0, TLS 1.1, and TLS 1.2 for Internet Explorer in Group Policy in this Microsoft article):
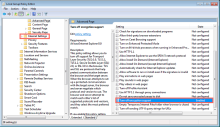
- Open Group Policy Management.
- In the Group Policy Management Editor, browse to .
- Double-click the Turn off Encryption Support setting to edit the setting.
- Click Enabled.
- In the Options window, change the Secure Protocol combinations setting to an appropriate setting that enables TLS 1.2 such as Use TLS 1.0, TLS 1.1, and TLS 1.2.
Note: It's important to check consecutive versions. Not selecting consecutive versions (for example, checking TLS 1.0 and 1.2 but not checking 1.1) could result in connection errors.
- Click OK.
Enable TLS 1.2 on .NET
TLS 1.2 is supported on .NET 4.6 and above. To determine the version of .NET installed on your system:
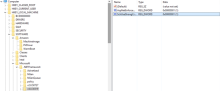
- Open the registry using regedit.exe.
- Go to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319
Note: The last number might be slightly different.
If that key is missing, .NET 4.6 is not installed.
- Under that key, search for key SKUs and look under it for .NETFramework,Version=v4.6.
If the key is not present, .NET 4.6 is not present on the system.
The link to .NET 4.6.2 installer is: https://www.microsoft.com/en-us/download/details.aspx?id=53344.
To set TLS 1.2, edit the registry as follows:
- Open the registry using regedit.exe.
- Go to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319.
Note: The last number might be slightly different.
- Add SchUseStrongCrypto registry DWORD under .NET 4.0 registry option, as shown below.
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319]
"AspNetEnforceViewStateMac"=dword:00000001
"SchUseStrongCrypto"=dword:00000001
If you're using ADFS, you must restart the service after you enable TLS 1.2 on .NET.
Related topics
Supported operating systems and browsers
Silently install the Okta Browser Plugin