Integrate multiple AWS instances
Connecting multiple Amazon Web Services (AWS) accounts using the API isn't supported. Follow the instructions in this section to use groups to manage roles for multiple AWS accounts.
The following diagram illustrates the three steps to perform to connect multiple Amazon Web Services (AWS) instances to Okta:
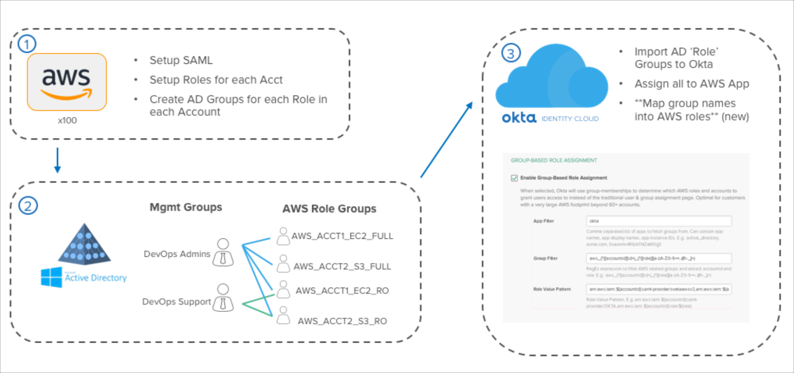
Set up AWS for SAML
Configure each AWS account for SAML access. Add Okta as a trusted IdP to the AWS account, and then create a trust relationship for each role that permits access through the new IdP. These are the same steps that you follow to provide SAML SSO into any single AWS account. Repeat these steps across all of your accounts. For advanced organizations, you can automate this process using Cloud Formation or AWS API scripts to perform a simple SAML setup in each account.
Create a management layer of groups in an external directory
After you configure SAML, create AWS role groups in an external directory for each role and account that you want users to access using Okta. You can do this three ways: Use a script between AWS and an external directory, export a CSV file to an external directory and then use a script against that file on the external directory side, or create the roles manually.
Next, create a link between the AWS role-specific groups and other external directory groups. Do this by assigning management groups as members of the AWS role groups that you want to grant access to. Assign users to the management groups to allow them access to the AWS roles and accounts for which the management group is a member.
Configure the AWS app in Okta for group-based role assignment
In Okta, import both the external directory management groups and the AWS role groups using the appropriate Okta external agent.
Next, assign your management groups to the AWS application that you set up in the first step. This assigns the proper users to the AWS app.
Finally, set up group-based role assignments. This is done to translate the names of each of your AWS role groups into a format that AWS can consume to list user roles on the Role Picker page.

