Risk scoring
Advanced risk scoring is available through Identity Threat Protection with Okta AI. If your org has ITP enabled, refer to Session protection and Entity risk policy instead.
Risk scoring uses a data-driven risk engine to determine whether a sign-in event is likely to represent malicious activity. Okta assigns a risk level to each sign-in attempt by evaluating information such as the following:
- The IP address used to make the sign-in request
- Behavioral information about the user who made the sign-in request
- Previous successful and failed sign-in attempts
- Routing information associated with the request
Using this information, you can configure custom sign-on policies for different scenarios based on the risk level. If a sign-in attempt is identified as "high" risk, you can configure the sign-on policy to require extra authentication before granting access.
The risk engine automatically identifies all new user sign-on attempts as "high" risk events. With each subsequent successful sign-in attempt, the risk engine gathers more information about the user's sign-in activity and patterns and evaluates subsequent sign-in attempts relative to this baseline.
For accurate risk evaluation and mitigation, trusted apps must send a valid deviceToken to Okta.
Risk scoring is designed to complement and not replace existing security tools. Don't use it for the following activities:
- Substitute bot management or automation detection
- Replace web application firewalls
- Assist with any type of security compliance
Risk-related information in System Log events
System Log events record information about how the risk level was determined for each authentication attempt. For example, the risk level for a sign-in event might be based on any combination of the following factors:
- Anomalous location
- Anomalous device
- Suspected threat based on Okta ThreatInsight detection
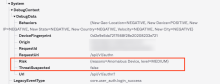
To see details about the risk evaluation for an event, go to DebugContext and DebugData.
In this example, the risk level for this sign-in attempt is MEDIUM because the user signed in using a new device, as indicated by reasons=Anomalous Device.
You might notice that the ThreatSuspected field is false even though the risk level is MEDIUM. If this sign-in attempt was from an IP address suspected of potentially malicious activity, the ThreatSuspected field would display true.
You can also query the System Log to view all events with a specific risk level. For example, to see a list of events identified as MEDIUM risk level, you can filter the System Log using the following query:
debugContext.debugData.risk co "level=MEDIUM"
To see a list of events identified as HIGH risk level, you can filter the System Log using the following query:
debugContext.debugData.risk co "level=HIGH"
To see a list of events identified as LOW risk level, you can filter the System Log using the following query:
debugContext.debugData.risk co "level=LOW"
By default, Okta evaluates all sign-in requests for risk and changes in user behavior. The results of the risk and behavior evaluation are added to the DebugContext section in the System Log in the LogOnlySecurityData field. See Risk and behavior evaluation.
Identity Threat Protection events in System Log
Identity Threat Protection with Okta AI is a continuous identity threat solution that responds to threats as they happen. It receives risk signals through the Okta risk engine and through security events providers, and records events when it detects a change in a user's session context or entity risk level.
Some Identity Threat Protection events are available to orgs with Adaptive MFA enabled. To view them in System Log, you must be directly assigned the super admin role (no group assignments).
- user.risk.detect appears when an entity's risk level changes.
- user.session.context.change appears when Okta identifies a change in a user's session context, device context, or IP address (unless the resulting IP address is in a trusted proxy).
- security.events.provider.receive_event appears when Okta receives a risk signal from a security events provider.
To learn more about risk scoring with ITP, see Session protection and Entity risk policy.
Configure risk scoring
You can add risk scoring as a condition for any app sign-in policy rule or global session policy rule by setting the AND Risk is field for a rule to Low, Medium, or High. The risk level is set to Any by default.
Follow these steps to configure risk scoring.
- Create a global session policy and configure the rule for it. See Create a global session policy.
- Create an app sign-in policy and configure the rule for it. See Add an app sign-in policy rule.
- Select the AND Risk is condition, then select a risk level and save the rule.