Trusted app filters
Trusted app filters for Okta FastPass allows orgs to manage which apps can invoke Okta FastPass in Windows, and in Chrome and Firefox for macOS. Specifically, trusted app filters enable the blocking of unsigned binaries and creating an allowlist of binaries. By preventing unsigned binaries from invoking Okta FastPass, you enhance security against unauthorized or malicious software. Creating an allowlist of binaries allows you to specify which binaries are permitted to invoke Okta FastPass, ensuring that only trusted apps have this ability.
Enable trusted app filters
Early Access release. See Enable self-service features.
Trusted app filters for Okta FastPass is an Early Access feature that you can enable in the Admin Console.
After the feature is enabled, you can create your queries using Okta Expression Language.
Configure trusted app filters
Locate the binaryIdentifier
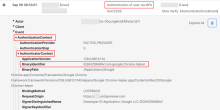
You can control which binaries or apps can invoke the Okta FastPass loopback server by configuring a query using Okta Expression Language in your authentication policy. Building the query requires the binaryIdentifier of the app that you want to block or allow. This information is found within System Logs.
- Open your System Logs and locate the log called Authentication of user via MFA .
- Scroll to the event .
- Copy the value of the binaryIdentifier to use in your query. For example, in Windows the binaryIdentifier for Chrome is Google Chrome. For macOS, the binaryIdentifier for Google Chrome is EQHXZ8M8AV.com.google.Chrome.helper.
Do this for each app that you want to allow or block from invoking Okta FastPass.
Build the query
You can control which binaries or apps can invoke the Okta FastPass loopback server by configuring a query using Okta Expression Language in your authentication policy.
| Query | Description | Example |
|---|---|---|
| Binding type |
The binding method used in authentication. Currently, LOOPBACK and APPLE_SSO_EXTENSION are the only binding methods supported. This feature isn't included in the Apple App Store version of Okta Verify for macOS. Download Okta Verify for macOS from the Admin Console at . |
|
|
Validation status |
This represents whether the binaries are signed or not. If a binary is signed, then it can be represented as a SUCCESS. This is only supported for LOOPBACK binding on macOS and Windows. |
device.caller.validationStatus == "SUCCESS" |
|
Binary/application identifier |
This identifies the app that you want to allow to invoke Okta FastPass. The binary that identifies applications can be found within System Logs. Ensure that the value is copied and pasted exactly as shown to avoid errors. |
|
You can combine the queries together in your authentication policy to block the unsigned app from invoking the loopback server:
device.caller.bindingType == "LOOPBACK" &&
device.caller.validationStatus == "SUCCESS" &&
(device.caller.binaryIdentifier == "EQHXZ8M8AV.com.google.Chrome.helper" || device.caller.binaryIdentifier == "43AQ936H96.org.mozilla.firefox")The resulting query is added to your app sign-on policy in the Expression Language field.
Trusted app filters are effective when the binding type is set to loopback. Ensure that this setting is configured correctly for the feature to work as intended.
Block unsigned binaries
-
In the Admin Console, open and click the policy that you want to edit.
-
Click the Actions dropdown menu beside the Rule that you want to add the EL query to, and click Edit. Optionally, create a rule in your global session policy and add your EL query there. See Global session policies.
-
In the Expression Language field, enter your query to block unsigned apps from invoking Okta FastPass: device.caller.validationStatus == SUCCESS
- Paste this query into all authentication policies for the apps that you want to secure from local attacks targeting Okta FastPass.
- Click Save.
Create and manage an allowlist of binaries
- In the Admin Console, open and click the policy that you want to edit.
- Click the Actions dropdown menu beside the Rule that you want to add the EL query to, and click Edit. Optionally, create a rule in your global session policy and add your EL query there. See Global session policies.
- In the Expression Language field, write an EL query to allow specific apps to invoke Okta FastPass. Copy the values shown for the binaryIdentifier field from the System Log to build the query. For example, to add Google Chrome to an allowlist, the EL query would read device.caller.binaryIdentifier == "EQHXZ8M8AV.com.google.Chrome.helper", where EQHXZ8M8AV.com.google.Chrome.helper is the value obtained from the System Log.
- Click Save.
Related topics
Add a custom expression to an authentication policy