Configure the user verification type for Okta Verify for Windows
You can configure the user verification type for Okta Verify using the UserVerificationType option when you deploy the app.
To change the user verification type after deployment, reinstall Okta Verify with the changed configuration. See Okta Verify configurations for Windows devices.
Authenticator operation mode
The default user verification type depends on the AuthenticatorOperationMode option:
|
Authenticator operation mode |
Default UserVerificationType option |
|---|---|
|
Normal This is the default mode. |
WindowsHello |
|
VirtualDesktopStatic |
OktaVerifyPasscode |
|
VirtualDesktopLayered |
OktaVerifyPasscode |
Physical systems
If you deploy Okta Verify on physical machines, such as laptops or desktops, and don't pass any configuration option, the user verification defaults to Windows Hello.
To change this default, set the UserVerificationType option to OktaVerifyPasscode. This setting prompts users to create a passcode in Okta Verify during enrollment.
Virtual systems
If you deploy Okta Verify in a virtual environment, set the AuthenticatorOperationMode option to either:
-
VirtualDesktopStatic: For environments where the user is assigned the same virtual machine each time they start a session.
-
VirtualDesktopLayered: For environments where the user is randomly assigned a virtual machine each time they start a session.
For virtual systems, UserVerificationType defaults to OktaVerifyPasscode. This setting prompts users to create a passcode in Okta Verify during enrollment.
See Configure Okta Verify for physical or virtual Windows environments.
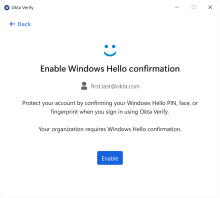
User verification with Windows Hello
When you set the UserVerificationType option to WindowsHello, Okta Verify prompts users to enable Windows Hello confirmation during enrollment.
If the app sign-in policy requires two factor types for user verification, Okta Verify prompts users to confirm their identity with Windows Hello biometrics or PIN.
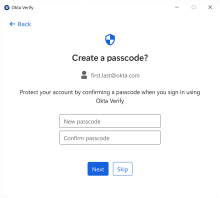
User verification with an Okta Verify passcode
Starting with version 4.9.0, Okta Verify for Windows supports user verification with an Okta Verify passcode.
The passcode is securely stored by the Windows operating system, not Okta Verify.
To enable this option, set the UserVerificationType option to OktaVerifyPasscode.
When a user is required to create or change their passcode for Okta Verify, the passcode must meet the minimum requirements for complexity:
-
At least eight characters.
-
No simple passcodes. Okta checks passcodes for pattern complexity and prevents users from setting simple passcodes.
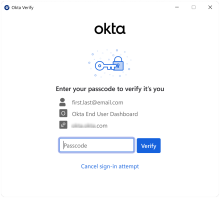
When the app sign-in policy requires two factor types for user verification, Okta Verify prompts users to confirm their identity with the passcode that they created during enrollment.
The user has three attempts to enter the correct passcode.
Related topics
Okta Verify configurations for Windows devices
Configure Okta Verify for physical or virtual Windows environments