Sign-in flows
The sequence of a sign-in flow depends on the authentication requirements that you set in your global session and app sign-in policies. The global session policy defines access globally, across all apps in your org, and the app sign-in policies enforce user authentication in the context of the requested app.
The user's location and profile are verified using both policies' group membership and authentication criteria. When a user is allowed to sign in without a password, Okta attempts to optimize the sign-in experience. If the device is enrolled with Okta Verify and a biometric authenticator is enabled, the biometric authenticator is always the first factor used for user authentication.
If users are required to sign in with a password, the password-first prompt always appears. This is true for any app sign-in policy configuration where the password authenticator is defined along with other authenticators.
Password / IDP
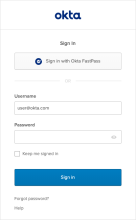
If any global session policy rule has the primary factor set to Password / IDP, users see the password-first Sign-In Widget.
-
Users enter their full app Username, including the domain, and then their password in the Password field. If you enabled the Multiple Identifiers EA feature, users can enter one of the configured identifiers instead of their username.
The Keep me signed in checkbox retains their identifier as well as authenticator verification information on their device for the amount of time designated by the global session policy rule.
-
Users click Sign in to initiate the authentication process.
-
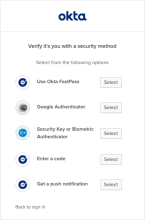
On the security method page, users pick one of the primary authenticator options allowed by the combined global session and app sign-in policy.
-
After clicking Select to choose an authenticator, users move to the verification step where they supply the required authenticator and then click Verify.
IdP users also see the Stay signed in and Don't stay signed in options when they're redirected back to Okta. After they make a selection, the option is hidden the next time they sign in.
Password / IDP / any factor allowed by app sign on rules
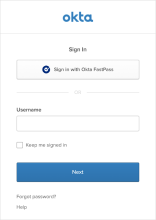
If any global session policy rule has the primary factor set to Password / IDP / any factor allowed by app sign on rules, users see the identifier-first Sign-In Widget as the first screen during their access flow.
-
Users enter their full app Username, including the domain, and then click Next. If you enabled the Multiple Identifiers EA feature, users can enter one of the configured identifiers instead of their username.
The Keep me signed in checkbox retains their identifier as well as authenticator verification information on their device for the amount of time designated by the global session policy rule.
-
On the security method page, users pick one of the primary authenticator options allowed by the combined global session and app sign-in policy.
-
After clicking Select to choose an authenticator, users move to the verification step where they supply the required authenticator and then click Verify.
IdP users also see the Stay signed in and Don't stay signed in options when they're redirected back to Okta. After they make a selection, the option is hidden the next time they sign in.