Farm addendum
This topic describes how to install the Okta Active Directory Federation Services (ADFS) Adapter in a Federation Server Farm environment.
Background
The installer stores the client secret as a protected string in the configuration file on each node. This protected string is generated using a machine-specific key.
When ADFS is used in a server farm, the configuration file is replicated across farm member servers.
Process overview
- If you're installing the adapter on servers in an ADFS farm, identify the primary node in the farm.
- Install the ADFS adapter on all nodes in the farm. Don't register the plugin during the installation. See Install the Okta ADFS Plugin on your ADFS Server.
- Create a farm configuration file by combining the clientSecret values into an array that contains the values from all the nodes in the farm.
- Manually register the ADFS Authentication Provider on the primary farm node.
Install the ADFS adapter
- Install the plugin on all the nodes in the ADFS farm, but don't register it with ADFS. At the Register Okta ADFS Adapter step of the installation, clear the Register Okta ADFS Adapter checkbox.
- On the primary node on the farm, open this file with a text editor:
C:\Users\<adfs_service_account_name>\AppData\Local\Okta\Okta MFA Provider\config\okta_adfs_adapter.json
- Copy the contents of the file into a new file, like okta_adfs_farm.json.
-
Combine the values in a modified configuration file. From each of the nodes in the farm, open the plugin configuration file and copy the clientSecret value:
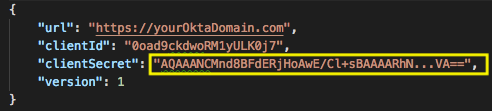
The clientSecret value of your okta_adfs_farm.json file should be a JSON array of protected strings:
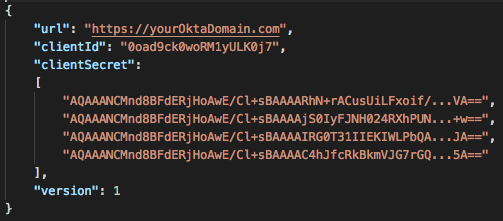
- Optional. Use a JSON lint tool to validate the JSON file.
- Manually re-register the ADFS Authentication Provider on the primary node. Use this script as an example. Replace the locations and name of the configuration file with your own:
[System.Reflection.Assembly]::Load("System.EnterpriseServices, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a") # change the values if needed $BinDir = "C:\Program Files\Okta\Okta MFA Provider\bin" $ConfigDir = "C:\Program Files\Okta\Okta MFA Provider\config" # we need the service to run in order to use powershell commands Start-Service adfssrv # Remove Okta MFA Provider $providers = (Get-AdfsGlobalAuthenticationPolicy).AdditionalAuthenticationProvider $providers.Remove("OktaMfaAdfs") Set-AdfsGlobalAuthenticationPolicy -AdditionalAuthenticationProvider $providers # Unregister Unregister-AdfsAuthenticationProvider -Name "OktaMfaAdfs" -Confirm:$false -ErrorAction Stop # restart the ADFS service Restart-Service adfssrv -Force # register MFA adapter again $OktaMfaAssamply = [Reflection.Assembly]::Loadfile($BinDir + "\OktaMfaAdfs.dll") $typeName = "OktaMfaAdfs.AuthenticationAdapter, OktaMfaAdfs, Version=" + $OktaMfaAssamply.GetName().Version + ", Culture=neutral, PublicKeyToken=3c924b535afa849b" # change the file name if needed Register-AdfsAuthenticationProvider -TypeName $typeName -Name "OktaMfaAdfs" -Verbose -ConfigurationFilePath "$ConfigDir\okta_adfs_farm.json" # restart the service Restart-Service adfssrv -Force # Enable Okta MFA adapter $providers = (Get-AdfsGlobalAuthenticationPolicy).AdditionalAuthenticationProvider $providers.Add("OktaMfaAdfs") Set-AdfsGlobalAuthenticationPolicy -AdditionalAuthenticationProvider $providers
-
Restart the ADFS service on all nodes to update the content of the configuration database.

