Configure optional settings
Cisco Advanced Server Access (ASA) IKEv2 VPN supports two optional settings:
Configure client IP reporting
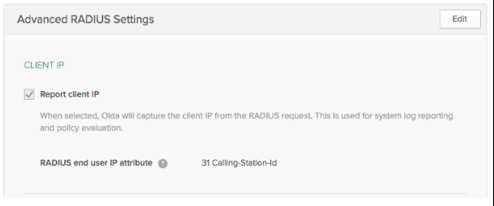
To configure Okta to be able to parse, report on, and eventually enforce policy based off the source client IP, you need to configure the Cisco ASA VPN (RADIUS).
-
In the Okta Admin Console, select the RADIUS app.
-
In the Sign On tab, select Advanced RADIUS Settings.
- Under Client IP, select Report client IP.
- For the RADIUS end user IP attributes: 31 Calling-Station-Id.
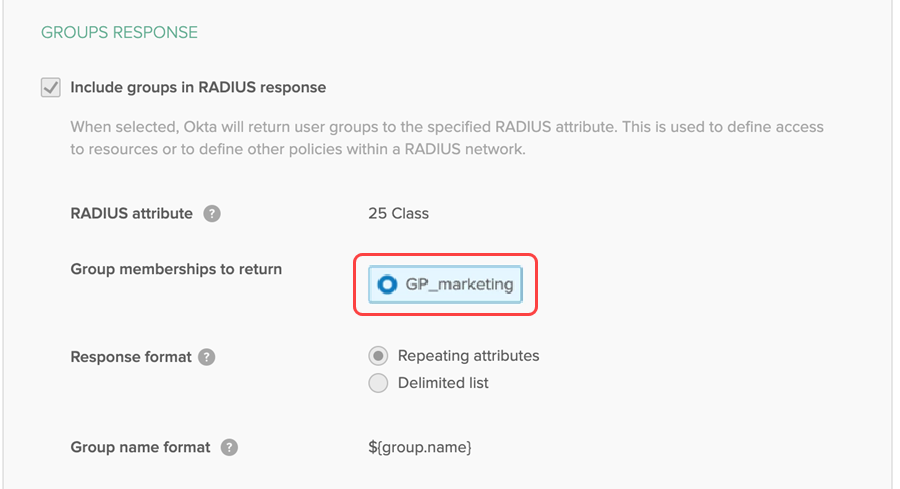
Configure groups response
The app can receive and parse groups on the standard attribute value pairs of 11 (Filter-Id) and 25 (class). Configure the Cisco ASA VPN (RADIUS) app in Okta as follows:
-
In the Okta Admin Console, select the RADIUS app.
-
In the Sign On tab, select Advanced RADIUS Settings.
-
In the Groups Reponse section, configure the following settings: