Desktop MFA for Windows
Use Desktop MFA to strengthen the security of users' authentication to Windows computers, enforcing MFA to sign in to a managed computer, virtual machine, or server that's joined to Active Directory or Entra ID. Admins can enable a passwordless sign-in experience for users, deploy Desktop MFA using an existing device management tool, and enable users to self-service password reset from the sign-in page.
Desktop MFA enforces multifactor authentication when users sign in to their Active Directory or Entra ID-managed Windows or locally managed macOS desktops or laptops.
How it works
In the following example, users securely sign in to their Windows device with Desktop MFA while offline.
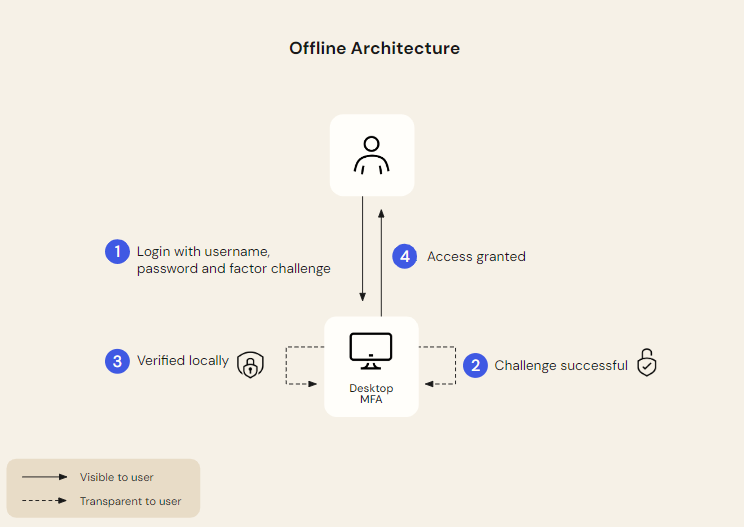
-
The offline user provides their device password and a factor challenge (for example, push notification or biometrics).
-
Okta validates the factor challenge.
-
The user's credentials are validated locally.
-
The user is signed in to their Windows device.
Even while offline, Desktop MFA users can securely access apps and data on their registered Windows device.

