Integrate with a company that uses Okta
If the company you acquired uses Okta, you can set up a hub-and-spoke environment and sync users and groups with the Okta Org2Org app. This approach enables employees from the acquired company to immediately access resources in the parent org. To authenticate, users don't have to change their usernames, reset their passwords, or enroll in multifactor authentication. The hub-and-spoke model provides companies with the flexibility to keep business systems separate as long as needed.
Topology
The hub-and-spoke model consists of the following components.
Hub
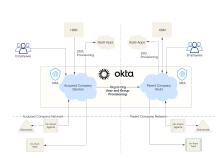
The hub is a single Okta org that operates as an independent service provider (SP) to the spokes. The hub provides user directory, authentication, and authorization services to spokes in a centralized manner. The hub also acts as an identity provider (IdP), integrating with downstream applications to provide secure Single Sign-On (SSO) and provisioning. If your company acquired another organization, and you want to grant employees of the acquired company access to your apps, your Okta org is hub. The hub is also called target org.
Spoke
A hub-and-spoke model can include one or more spokes. A spoke operates as an independent IdP. It provides user directory, authentication, and authorization services for users within the spoke in a decentralized manner. Spokes can be Okta orgs that use their own instance of Okta Universal Directory and store user profile and group information. This information can be created directly in Okta or sourced from repositories such as Active Directory, LDAP, or other IdPs (for example, HR applications). The acquired company's Okta org is referred to as the spoke or source org.
Okta Org2Org app
The Org2Org app integrates an acquired company's Okta org (spoke) with the parent company's Okta org (hub). Users and groups of the spoke are provisioned into the hub. Profile sync occurs in real time and it supports both push and pull operations. Any attributes can be synced and you can selectively source user profile attributes from either the hub or the spoke orgs, allowing for robust provisioning of spoke users into applications configured in the hub. This allows employees of the acquired company to access resources in the parent company.
The following figure is an example of an Okta hub-and-spoke environment. The parent company is the hub. The acquired company is the spoke.
Workflow
In this example, you give employees from the acquired company access to your Google Workspace app, which is configured in your Okta org (hub org). For the step-by-step procedure, go to Integrate Okta Org2Org with Okta.
This is the high-level workflow:
-
In the spoke org, add and configure the Okta Org2Org app to authorize and authenticate users to the hub.
-
In the hub org, create a SAML IdP to allow federation from the spoke to the hub.
-
In the hub org, create a group for each spoke org.
-
In the hub org, configure Google Workspace to share it with users from the spoke org. Assign the app to the groups that contain users from the spoke org.
-
Optional. Configure provisioning in the spoke only if you need to provision users from downstream shared applications into the hub.
-
If you don't need provisioning, disable account linking when you configure your IdP in the hub.
-
If you need provisioning but don't need real-time sync of users, user profile attributes, and groups, create spoke org users in the hub org manually.
-
If you need provisioning and real-time sync of users, enable provisioning in the Okta Org2Org app.
-
Best practices
When you configure the SAML IdP in the hub org, disable account linking if possible. If you need account linking, consider these Security best practices.