Add a device assurance policy
You can define one or more device attributes that you want to evaluate for each platform that you support. There's no limit to the number of device assurance policies that you can add, but each policy must have a unique name.
-
In the Admin Console, go to .
-
Click Add a policy.
-
In the Add device assurance policy section, enter the following information:
-
Policy name: Specify a unique name for the set of device attributes that you want to define.
-
Platform: Select the device platform that you want to set device conditions for.
As device assurance conditions are platform-specific, you must create separate app sign-in policies for each platform.
For example, if you add device assurance for Windows to an app sign-in policy, the rule isn't matched when a user accesses the app from a macOS device.
-
Device attribute providers: Choose whether your policy uses Okta Verify, Chrome Device Trust, or both services as the posture provider. If you select both providers, there may be some overlap in signals. In this scenario, the signal from Okta is given priority.
-
-
Select platform-specific conditions.
- Configure remediation.
-
Click Save.
Three signals can be collected from either Okta Verify or Chrome Device Trust. When you select both Okta Verify and Chrome Device Trust as device posture providers, the following signal attributes appear in the Okta Verify section of the device assurance policy:
- Minimum OS version
- Screen lock
- Disk encryption
Ensure that you select the appropriate attribute for the device assurance policy you're creating.
Platform-specific device assurance conditions
Set device assurance conditions according to the platform and device attribute providers that you select: Android, ChromeOS, iOS, macOS, or Windows.
With the dynamic operating system (OS) version compliance feature, you can set a condition where an OS version replaces the Minimum version option. You can then configure static or dynamic versions for your assurance policies.
To help you configure OS conditions, Okta maintains OS definitions:
-
Okta adds new major OS versions and security patches when the OS vendors release them.
-
If a vendor no longer issues security updates for a major OS version, Okta removes that version from the OS definition.
Android
- Minimum Android version: Select a preset version from the list or specify a custom version. To specify a custom version, enter an Android version and optionally a security patch. When this policy is evaluated, the version component is evaluated first. If the version of the device matches the version in your policy, the security patch component is evaluated next.
- OS version: Specify the OS requirements for your assurance policy.
- If you select a static version (for example, OS version must be at least 12), this condition persists until you update the assurance policy. You can also specify a custom version.
- If you select a dynamic version (for example, OS version must be at least the latest supported major version), the condition is relative to the latest major OS release. When a new OS version is released, Okta updates the OS definitions. As a result, you can ensure that users are always on the latest OS version without updating your device assurance policy. See Okta Device Assurance: Supported OS levels.
-
Lock screen: If you select this option, the device must have a screen lock. Also, select this checkbox if biometrics is required.
-
Disk encryption: If you select this option, the device disk must be encrypted. Devices with Android 8 or 9 support full-disk encryption. Devices with Android 10 or later support full-disk encryption only if upgraded from a previous version. Devices with Android 10 and later use file-based encryption.
-
Hardware keystore: If you select this option, the device must support hardware-backed keys.
-
Rooting: If you select this option, it Okta denies access on rooted devices.
If you use Android Device Trust as the device posture provider, you can configure the following device attributes in addition to the platform attributes:
-
Enforce latest major OS updates available to device: This condition is available if you enabled the Dynamic OS version compliance Early Access feature and set the OS requirement to a dynamic version such as OS version must be at least the latest supported major version.
- Lock screen: Configure the screen lock complexity: None, Low, Medium, or High.
- Google Play Protect: Select the checkbox to make Google Play Protect scans mandatory. Users who disabled scan services on their devices are prompted to enable them again. Configure the maximum risk threshold of the scan:
- Low: No issues were found. This is the most secure option.
- Medium: The scan detected potentially harmful apps.
- High: The scan detected harmful apps or the scan wasn't evaluated. This is the least secure option.
- Device integrity level: Select any of the following options:
- None: Default. The device integrity isn't evaluated during authentication. Change this value if you want the policy to check the device integrity.
- Basic: The device passes basic system integrity checks. Devices on Android 13 or later require Android Platform Key Attestation. The device may not meet Android compatibility requirements and may not be approved to run Google Play services. For example, the device may be running an unrecognized version of Android.
- Standard: The app is running on an Android-powered device with Google Play services. The device passes system integrity checks and meets Android compatibility requirements.
- Strong: The device has Google Play services and a strong guarantee of system integrity according to Android compatibility requirements. Devices on Android 13 or later must have had a security update in the last year.
- USB debugging: Select the checkbox to ensure that USB debugging is disabled. If the user's device doesn't comply with this requirement, they're prompted to turn off debugging from Developer Options.
- Network proxies: Select the checkbox to ensure the user's device doesn't use a network proxy.
- WiFi network security: Select the checkbox to ensure that users access their apps on a secure wireless network. If the network isn't secure, users are prompted to use mobile data to access the Okta-protected resource.
ChromeOS
-
Device management: Select this option if the device must be enrolled in ChromeOS device management.
-
Minimum ChromeOS version: Enter the minimum version details for ChromeOS.
-
Disk encryption: Select this option if the device disk must be encrypted.
-
Firewall: Select this option if a firewall must be enabled.
-
Screen lock password: If you select this option, the device requires a password to unlock.
-
Screen lock: Select this checkbox to permit screen locking.
-
Minimum Chrome browser version: Enter the minimum version details for the Chrome browser version allowed by the policy.
-
Device enrollment domain: Add the domain for device enrollment.
-
Chrome DNS client: Select this checkbox if the Chrome DNS client must be enabled.
-
Chrome Remote Desktop app: Select this checkbox if the Chrome Remote Desktop app must be blocked.
-
Safe Browsing protection level: Use the dropdown menu to select a preset value.
-
Site Isolation: Select this checkbox if Site isolation must be enabled.
-
Password protection warning: Use the dropdown menu to select a preset value.
-
Enterprise-grade URL scanning: Select this checkbox if enterprise-grade URL scanning must be enabled.
-
Key trust level for ChromeOS: Select Device in verified mode from the dropdown menu.
iOS
- Minimum iOS version: Select a preset version from the list, or specify a custom version.
- OS version: Specify the OS requirements for your assurance policy.
- If you select a static version (for example, OS version must be at least iOS 15), this condition persists until you update the assurance policy. You can also specify a custom static version.
- If you select a dynamic version (for example, OS version must be at least the latest supported major version), the condition is relative to the latest major OS release. When a new OS version is released, Okta updates the OS definitions. As a result, you can ensure that users are always on the latest OS version without updating your device assurance policy. See Okta Device Assurance: Supported OS levels.
-
Lock screen: If you select this option, the device requires a passcode. Also, select the option if Touch ID or Face ID is required.
-
Jailbreak: If you select this option, Okta denies access on jailbroken devices.
macOS
- Minimum macOS version: Select a preset version from the list, or specify a custom version.
- OS version: Specify the OS requirements for your assurance policy.
- If you select a static version (for example, OS version must be at least Monterey (12)), this condition persists until you update the assurance policy. You can also specify a custom version.
- If you select a dynamic version (for example, OS version must be at least the latest supported major version), the condition is relative to the latest major OS release. When a new OS version is released, Okta updates the OS definitions. As a result, you can ensure that users are always on the latest OS version without updating your device assurance policy. See Okta Device Assurance: Supported OS levels.
-
Lock screen: If you select this option, the device requires a password or Touch ID.
-
Disk encryption: If you select this option, the disk must be encrypted. This setting only checks for hardware disk encryption, and doesn't check for FileVault status. Only internal and system volumes are evaluated for disk encryption. Volumes that are hidden, removable, automounted, or used for recovery aren't evaluated.
-
Secure Enclave: If you select this option, the device must support Secure Enclave.
-
Join type: If you select this option, the device must be Okta-joined. This is required to enable Device-Bound Single Sign-On.
If you select Chrome Device Trust as the device posture provider, you can configure the following device attributes in addition to the platform attributes:
-
Firewall: Select this checkbox if a firewall must be enabled.
- Minimum Chrome browser version: Enter version details for the minimum Chrome browser version allowed by the policy.
-
Device enrollment domain: Add the domain for device enrollment.
-
Chrome DNS client: Select this checkbox if the Chrome DNS client must be enabled.
-
Chrome Remote Desktop app: Select this checkbox if the Chrome Remote Desktop app must be blocked.
-
Safe Browsing protection level: Use the dropdown menu to select a preset value.
-
Site Isolation: Select this checkbox if Site isolation must be enabled.
-
Password protection warning: Use the dropdown menu to select a preset value.
-
Enterprise-grade URL scanning: Select this checkbox if enterprise-grade URL scanning must be enabled.
-
Key trust level for Chrome: Select a preset value from the dropdown menu.
Windows
- Minimum Windows version: Select a preset version from the list or specify a custom version.
- OS version: Specify the OS requirements for your assurance policy.
- If you select a static version (for example, OS version must be at least Windows 11 (22H2)), this condition persists until you update the assurance policy. You can also specify a custom version.
- If you select a dynamic version (for example, OS version must be at least latest supported major version), the condition is relative to the latest major OS release. When a new OS version is released, Okta updates the OS definitions. As a result, you can ensure that users are always on the latest OS version without updating your device assurance policy. See Okta Device Assurance: Supported OS levels.
-
Windows Hello must be enabled: If you select this option, users must have Windows Hello enabled on their devices. However, users don't have to use Windows Hello or enter a password to sign in to apps.
-
Disk encryption: If you select this option, the disk must be encrypted. Only internal and system volumes are evaluated for disk encryption. Volumes that are hidden, removable, automounted, or used for recovery aren't evaluated for disk encryption.
-
Trusted Platform Module: If you select this option, the device must support a Trusted Platform Module.
-
Join type: If you select this option, the device must be Okta-joined. This is required to enable Device-Bound Single Sign-On.
If you select Chrome Device Trust as the device posture provider, you can configure the following device attributes in addition to the platform attributes:
-
Lock screen secured: Select this checkbox if the lock screen requires a password, Windows Hello, or a smart card.
-
Firewall: Select this checkbox if a firewall must be enabled.
- Minimum Chrome browser version: Enter version details for the Chrome browser version allowed by the policy.
-
Device enrollment domain: Add the domain for device enrollment.
-
Chrome DNS client: Select this checkbox if the Chrome DNS client must be enabled.
-
Chrome Remote Desktop app: Select this checkbox if the Chrome Remote Desktop app must be blocked.
-
Safe Browsing protection level: Use the dropdown menu to select a preset value.
-
Site Isolation: Select this checkbox if site isolation must be enabled.
-
Password protection warning: Use the dropdown menu to select a preset value.
-
Enterprise-grade URL scanning: Select this checkbox if enterprise-grade URL scanning must be enabled.
-
Secure Boot: Select this checkbox if Secure Boot must be enabled.
-
Windows machine domain: Enter the domain of the Windows machine.
-
Windows user domain: Enter a domain for user accounts.
-
Third party software injection: Select this checkbox if third-party software injection must be blocked.
-
CrowdStrike - Agent ID: Enter your CrowdStrike Agent ID. This value must be in lowercase and without hyphens.
-
CrowdStrike - Customer ID: Enter your CrowdStrike Customer ID. This value must be in lowercase and without hyphens.
-
Key trust level for Chrome: Use the dropdown menu to select a preset value.
-
Virus and threat protection enabled: Select this checkbox to enforce that the Windows Security Center's virus and threat protection setting is enabled on the device.
Configure remediation
Early Access release. See Enable self-service features.
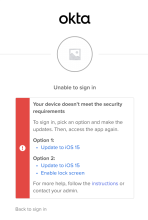
After you enable the Grace period for device assurance feature, you can configure remediation instructions to display in the Sign-In Widget.
-
Hide remediation instructions: The Sign-In Widget doesn't display remediation instructions for users who don't pass device assurance compliance.
-
Display remediation instructions: The Sign-In Widget displays remediation instructions for users who don't pass device assurance compliance.
You can grant users a period in which they can resolve the device noncompliance before they lose access to apps protected by the policy. Select a Grace period option:
-
No: With this default setting, users are denied access to apps if their devices don't meet the conditions of the device assurance policy. To regain access to the apps, users must complete the remediation instructions.
-
Yes, by a due date: Select a remediation due date. The remediation grace period expires at midnight GMT (+00:00) on the day that you select. In the Sign-In Widget, the remediation due date is calculated according to the user's time zone.
For example, if you configure a grace period with a due date of 09/05/2024 12:00 am GMT+00:00. Then users in Eastern Daylight Time receive the following message in the Sign-In Widget: Your device doesn't meet the security requirements. Fix the issue by 09/04/2024, 8:00 PM EDT to prevent lockout. Users who don't complete the remediation actions by this date and time are denied access to apps protected by the policy.
-
Yes, after a number of days: You can configure a grace period from 1 through 180 days. Users who don't complete the remediation actions by the date and time specified in the Sign-In Widget are denied access to the apps protected by the policy.
-
To turn off the Grace period for device assurance feature, change these configurations first:
- Remove the grace period settings you configured in any of your device assurance policies.
- Ensure that you have a consistent remediation setting across all device assurance policies.