Test the Check Point RADIUS integration
Test the Check Point RADIUS integration.
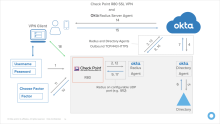
The detailed web sequence is listed below and shown in this diagram.
- User Logs in with Username/Password
- Gateway receives data and forwards via Radius to Okta RADIUS Server Agent
- Okta RADIUS Server Agent sends to Okta Identity Cloud
- Okta Identify Cloud Determines the Authentication source and responds or optionally forwards to on-prem directory agent
- Optional: Directory Agent sends Password to Directory
- Optional: Directory Confirms the password
- Optional: Directory Agent Confirms the password to Okta Identity Cloud
- Okta Identity Cloud evaluates the app sign-in policy and as required sends a message to the Okta RADIUS Server Agent to challenge the user for a factor
- The Okta RADIUS Server Agent relays the challenge message to the Gateway
- The Gateway displays a message to select a factor to the user
- User supplies the desired factor
- Gateway receives data and forwards via Radius to Okta RADIUS Server Agent
- Okta RADIUS Server Agent sends to Okta Identity Cloud
- Okta Identify Cloud evaluates the Choice and triggers the appropriate response (push message shown)
- Push message is received and Responded to by the user
- Success Message returned to the Okta RADIUS Server Agent
- Success Message returned to the gateway
- Connected
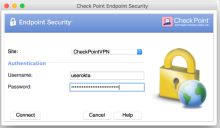
Test 1 - Connect a remote access VPN client to the gateway
- Download and install one of the latest VPN clients such as the Windows client described in the Remote Access Solutions sk67820. For example, the E80.82 Remote Access Clients for Windows.
- Enter the server address, then click Next. Select Standard.
- Select Username and Password as the Authentication Method.
- Click Finish, then Connect.
- Enter your Okta username and password. If multifactor authentication is setup, follow the prompts to complete the Challenge-Response process.
-
Verify your machine is assigned a virtual interface with IP address belonging to network 172.16.10/24.
-
(Optional): Verify that you can access the web server in the private network behind Check Point.
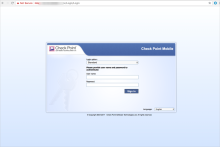
Test 2 - Browser access to the Check Point Mobile Access SSL VPN portal