Enforce Device Trust and SSO for desktop devices with Okta + VMware Workspace ONE
Important
This integration supports only SP-initiated authentication flows. IdP-initiated flows (such as trying to access resources by clicking SAML apps on the Okta End User Dashboard) are not supported.
This use case allows administrators to establish device trust by evaluating device posture, such as whether the device is managed, before permitting end users to access sensitive applications. It also establishes Okta as a trusted identity provider to Workspace ONE, allowing end users to log in to the Workspace ONE app, Workspace ONE Intelligent Hub app, and web portal using Okta app sign-in policies.
Authentication flow for macOS and Windows devices:
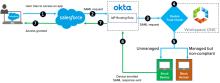
A device trust flow for macOS and Windows 10 devices using the Salesforce application would follow this sequence:
- End user attempts to access the Salesforce tenant (SP-init only. IdP-init is not supported. See Notes).
- Salesforce redirects to Okta as the configured identity provider.
- Okta processes the incoming request and routes the client to the Workspace ONE IdP based on configured routing rules.
- Workspace ONE challenges the client device for credentials.
- Workspace ONE checks the device compliance status. Workspace ONE blocks access if the device is managed but not compliant. If the device isn't managed, Workspace ONE prompts for device enrollment. Note that Device Trust and access policies for desktop devices are defined in VMWare.
- Upon successful authentication with Workspace ONE, the client device is redirected back to Okta.
- Okta validates the SAML assertion from Workspace ONE and issues the SAML assertion for Salesforce.
To configure this use case:
Step 1: Configure VMware Identity Manager as an Identity Provider in Okta
Step 2: Configure Okta application source in VMware Identity Manager
Step 3: Configure Device Trust and Access Policies in VMware for desktop devices