Integrate Okta Device Trust with Omnissa Workspace ONE for Windows and macOS computers
This Okta and Workspace ONE integration for desktop devices is based primarily on SAML trust connections. It allows administrators to establish device trust by evaluating device posture before permitting end users to access sensitive applications. To determine whether devices are managed and compliant, device posture policies established in Workspace ONE are evaluated anytime a user tries to access a protected application.
You can also configure this integration to provide end users a streamlined device enrollment experience, leverage Okta's extensible Multifactor Authentication to applications in Workspace ONE, and provide a consistent and familiar login experience for users and administrators.
This guide provides step-by-step instructions to configure and test use cases supported by Okta and Workspace ONE. To integrate Okta with Workspace ONE, you integrate Workspace ONE Access with Okta. Workspace ONE Access is the identity component of Workspace ONE.
This integration supports only SP-initiated authentication flows. IdP-initiated flows (such as trying to access resources by clicking SAML apps on the Okta End User Dashboard) are not supported.
Use Cases
The main use cases supported by the Okta + Workspace ONE integration include:
- Enforce Device Trust and SSO for desktop devices with Okta and Omnissa Workspace ONE
- Configure streamlined Device Enrollment and Workspace ONE login for desktop devices using Okta
1. Enforce Device Trust and SSO for desktop devices with Okta and Omnissa Workspace ONE
Enforce Device Trust and SSO for desktop devices with Okta and Omnissa Workspace ONE
This use case allows administrators to establish device trust by evaluating device posture, such as whether the device is managed, before permitting end users to access sensitive applications. It also establishes Okta as a trusted identity provider to Workspace ONE, allowing end users to log in to the Workspace ONE app, Workspace ONE Intelligent Hub app, and web portal using Okta app sign-in policies.
Authentication flow for macOS and Windows devices:
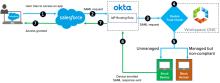
A device trust flow for macOS and Windows 10 devices using the Salesforce application would follow this sequence:
- End user attempts to access the Salesforce tenant (SP-init only. IdP-init is not supported. See Notes).
- Salesforce redirects to Okta as the configured identity provider.
- Okta processes the incoming request and routes the client to the Workspace ONE IdP based on configured routing rules.
- Workspace ONE challenges the client device for credentials.
- Workspace ONE checks the device compliance status. Workspace ONE blocks access if the device is managed but not compliant. If the device isn't managed, Workspace ONE prompts for device enrollment. Note that Device Trust and access policies for desktop devices are defined in VMWare.
- Upon successful authentication with Workspace ONE, the client device is redirected back to Okta.
- Okta validates the SAML assertion from Workspace ONE and issues the SAML assertion for Salesforce.
To configure this use case:
Step 1: Configure Workspace ONE Access as an Identity Provider in Okta
Step 2: Configure Okta application source in Workspace ONE Access
Step 3: Configure Device Trust and Access Policies in Workspace ONE for desktop devices
2. Configure streamlined Device Enrollment and Workspace ONE login for desktop devices using Okta
Configure streamlined Device Enrollment and Workspace ONE login for desktop devices using Okta
You can configure this use case to provide end users a streamlined device enrollment experience, leverage Okta's extensible Multi Factor Authentication to applications in Workspace ONE, and provide a consistent and familiar login experience for users and administrators.
This configuration is configured in Workspace ONE Access, the identity component of Workspace ONE.
To configure this use case:
Optional: You can allow end users to access apps from either the Okta dashboard or the Workspace ONE dashboard. Both experiences are fully supported. You can configure the Workspace ONE catalog to publish applications federated through Okta without the need to first import them into Workspace ONE Access.
For details, see Publish Okta apps to the Workspace ONE catalog
Requirements
Ensure that your environment meets the following requirements before you begin the Workspace ONEand Okta integration.
Components
Workspace ONE
- A Workspace ONE Access tenant with System Administrator role
- A Workspace ONE Unified Endpoint Management (UEM) tenant
- Workspace ONE Access Connector
- Workspace ONE Access AirWatch Cloud Connector (ACC)
ACC is required only if you use Workspace ONE UEM.
Note: If your existing deployment syncs users to Workspace ONE Access from Workspace ONE UEM, the Workspace ONE Access connector is not required. For new deployments, using the Workspace ONE Access connector to sync users from Active Directory to Workspace ONE Access is recommended.
Okta
- An Okta org (tenant) with Super or Org Administrator role
- Device Trust for Workspace ONE enabled by Okta Support
- Identity Provider Routing Rules (IdP Discovery) enabled by Okta Support
Supported apps and devices
- Any Windows or macOS SAML or WS-Fed cloud app
- Devices running Okta-supported versions of Windows or macOS operating systems
Integrate Workspace ONE and Workspace ONE Access
Integrate your Workspace ONE UEM and Workspace ONE Access tenants and configure the mobile SSO authentication methods that you intend to use for device trust.
Notes
-
Only SP-initiated authentication flows are supported – This SAML-based integration supports only SP-initiated authentication flows. IdP-initiated flows (such as trying to access resources by clicking SAML apps on the Okta End User Dashboard) are not supported.
- Do not secure Workspace ONE with this Device Trust solution – Doing so will prevent new users from enrolling their device in Workspace ONE and accessing other device trust-secured apps.
- Timeout issue can cause an SSO error – End users signing in to device trust-secured apps from an untrusted device are prompted to enroll their device with Workspace ONE. (This is expected behavior.) But if the apps are native apps and Workspace ONE enrollment takes longer than 10 minutes, or if the end user waits longer than 10 minutes after enrollment before trying again to access the app, an SSO error occurs because the app session has timed out. Advise affected end users to try to access the app again.