Enable OpenID Connect with existing Active Directory Federation Services apps
This topic describes how to enable OpenID Connect (OIDC) connections with existing Active Directory Federation Services (ADFS) apps.
Start this procedure
-
Enable an existing app to use OIDC:
-
In the Admin Console, go to .
- Select an ADFS app.
- Select the Sign On tab.
- In the Settings section, click Edit.
- Select OpenID Connect.
- Enter the Client ID and the Client secret.
- In the Redirect URI field, enter your redirect URI. Use a forward slash at the end of the URI, like https://yourdomain.com/.
- Click Save.
-
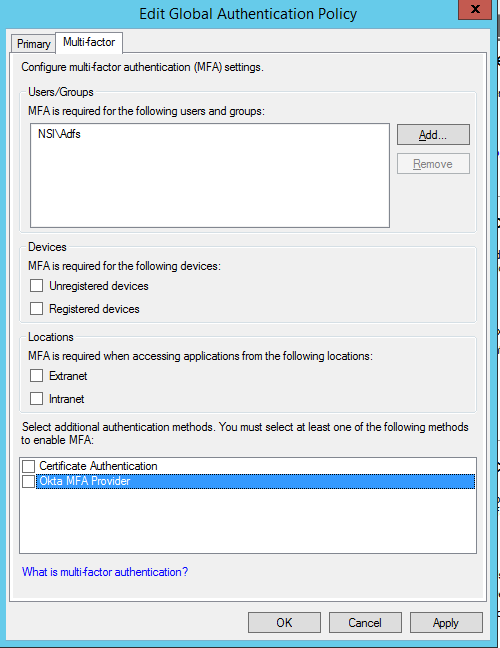
- Open the ADFS Global Authentication Policy for editing and then select the Multi-factor tab.
- Clear the Okta MFA Provider checkbox and then click OK before proceeding to the next step.
- Upgrade any existing ADFS plugins to version 1.7.0 or later.
- After the upgrade has finished, verify that your app functions normally.
- Open this file with a text editor:
C:\Users\<adfs_service_account_name>\AppData\Local\Okta\Okta MFA Provider\config\okta_adfs_adapter.json.
See Configure MFA for Active Directory Federation Services (ADFS).
- Search for the useOIDC property and set its value to true.
- Save your changes and close the text editor.
- Open this file with a text editor:
-
Using a text editor, copy and create the following Microsoft Powershell script and save as ApplyConfigurationSettingChanges.ps1. If required, change the values of the BinDir and ConfigDir variables to match your environment.Copy
ApplyConfigurationSettingChanges.ps1
# ApplyConfigurationSettingChanges.ps1
[System.Reflection.Assembly]::Load("System.EnterpriseServices, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a")
$BinDir = "C:\Program Files\Okta\Okta MFA Provider\bin"
$ConfigDir = "C:\Program Files\Okta\Okta MFA Provider\config"
Start-Service adfssrv
# Remove Okta MFA Provider
$providers = (Get-AdfsGlobalAuthenticationPolicy).AdditionalAuthenticationProvider
$providers.Remove("OktaMfaAdfs")
Set-AdfsGlobalAuthenticationPolicy -AdditionalAuthenticationProvider $providers
# Unregister
Unregister-AdfsAuthenticationProvider -Name "OktaMfaAdfs" -Confirm:$false -ErrorAction Stop
# restart the ADFS service
Restart-Service adfssrv -Force
# register MFA adapter again
$OktaMfaAssamply = [Reflection.Assembly]::Loadfile($BinDir + "\OktaMfaAdfs.dll")
$typeName = "OktaMfaAdfs.AuthenticationAdapter, OktaMfaAdfs, Version=" + $OktaMfaAssamply.GetName().Version + ", Culture=neutral, PublicKeyToken=3c924b535afa849b"
Register-AdfsAuthenticationProvider -TypeName $typeName -Name "OktaMfaAdfs" -Verbose -ConfigurationFilePath "$ConfigDir\okta_adfs_adapter.json"
# restart the service
Restart-Service adfssrv -Force
# Enable Okta MFA adapter
$providers = (Get-AdfsGlobalAuthenticationPolicy).AdditionalAuthenticationProvider
$providers.Add("OktaMfaAdfs")
Set-AdfsGlobalAuthenticationPolicy -AdditionalAuthenticationProvider $providers
- Open Microsoft PowerShell as an administrator and execute the script ApplyConfigurationSettingChanges.ps1.
- Verify that the user can authenticate.

