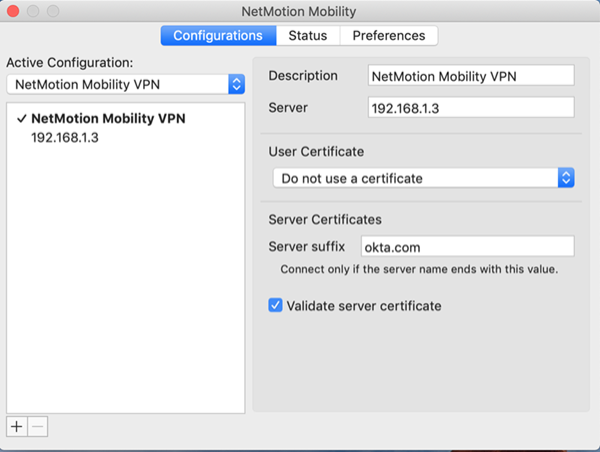
Configure NetMotion Mobility
Configure NetMotion mobility to use the Okta RADIUS Server Agent using the Okta Integration Network (OIN) NetMotion Moblity (RADIUS) app.
Before you begin
Meet the following network connectivity requirements before you install the Okta RADIUS agent:
| Source | Destination | Port/Protocol | Description |
|---|---|---|---|
| Okta RADIUS Agent | Okta Identity Cloud | TCP/443 HTTP |
Configuration and authentication traffic. |
| Client Gateway | Okta RADIUS Agent | UDP/1812 RADIUS (Default, you can change this when you install and configure the RADIUS app) | RADIUS traffic between the gateway (client) and the RADIUS agent (server). |
Supported Factors
The size of the challenge message can be too large for the RADIUS prompt if you let users enroll too many factors. Okta recommends that you enroll no more than eight factors at a given time.
Okta supports the following factors for RADIUS apps:
|
MFA Factor |
Password Authentication Protocol (PAP) | Extensible Authentication Protocol - Generic Token Card (EAP-GTC) | Extensible Authentication Protocol - Tunneled Transport Layer Security (EAP-TTLS)* |
|---|---|---|---|
| Custom TOTP Authentication | Supported | Supported | Supported - as long as challenge is avoided. For example MFA only or "Password, passcode". |
| Duo (Push, SMS, and Passcode only) | Supported | Supported | Duo passcode only. |
|
Supported |
Supported |
Supported when the string "EMAIL" is initially sent. |
|
| Supported | Supported | Supported, as long as challenge is avoided. For example MFA only or "Password, passcode". |
|
| Supported | Supported | Supported as long as challenge is avoided. For example: MFA-only or "Password, MFA" for TOTP. Push can work with primary authentication with MFA as the push challenge is sent out-of-band. |
|
|
Not supported |
Not supported |
Not supported |
|
|
RSA Token/ On-prem MFA |
Supported |
Supported |
Supported - as long as challenge is avoided. |
| Supported (Password and MFA only) | Supported (Password + MFA only). |
Not supported | |
| SMS authentication | Supported | Supported |
Supported when the string "SMS" is sent. Refer to associated note. |
| Symantec VIP | Supported | Supported | Supported - as long as challenge is avoided. For example MFA only or "Password, passcode". |
| Supported | Supported | Supported when the string "CALL" is sent. Refer to associated note. |
|
| Supported | Supported | Supported - as long as challenge is avoided. For example MFA only or "Password, passcode". |
* RADIUS supports three authentication methods:
- Password + MFA: Primary authentication using password, then the user is prompted to select factors to complete the authentication.
- MFA Only: Instead of password, users enter either a one-time passcode (OTP), or one of EMAIL, SMS, CALL, PUSH (case insensitive).
- Password and Passcode: Password entered immediately followed by a passcode in a request.
Must be in the same request, for example: Abcd1234,879890" or "Abcd1234,SmS".
Protocols support the following authentication methods:
| Protocol | Supports |
|---|---|
| PAP | Password and MFA, MFA, "Password and passcode". |
| EAP-TTLS | MFA only, "Password and passcode". |
| EAP-GTC | Password and MFA, MFA only, "Password and passcode". |
Users must send the specified string EMAIL/SMS/CALL, which initially returns a failure. This results in the generation of an OTP provided using the specified method. The provided OTP can then be used for authentication.
EAP-TTLS doesn't support enrollment
Authentication will fail unexpectedly when EAP-TTLS is enabled, either Okta Verify or Phone are specified as the required enrollment policy, and the user isn't enrolled in that factor.
U2F Security and Windows Hello aren't compatible with RADIUS-enabled implementations. See RADIUS applications in Okta and About multifactor authentication.
Passwordless authentication
RADIUS authentication uses passwords as the primary authentication mechanism. Traditional RADIUS authentication can't be performed with passwordless users. RADIUS can use other factors for authentication when the application setting property Okta performs primary authentication is cleared. See 2FA Only (Passwordless Mode) in RADIUS applications in Okta for addition detail.
Typical workflow
Perform the following tasks, in the order shown:
|
Task |
Description |
|---|---|
| Download the RADIUS agent |
|
| Install the Okta RADIUS Agent. | |
| Configure application |
|
| Configure NetMotion with the RADIUS settings |
|
| Add Trusted root CA |
|
| Verify Connection |
|