Google Workspace integration
Integrate Identity Security Posture Management (ISPM) with your Google Workspace.
- Create a project
- Create a service account
- Add roles to the service account
- Create keys for the service account
- Enable API access
- Configure domain-wide delegation for the service account
- Add ISPM IPs to your trusted IP range
- Share the parameters with ISPM
Before you begin
Ensure that you have the Google Workspace super admin privilege.
Create a project
-
Sign in to your Google Cloud Console as a super admin and click to open the Navigation menu.
-
Go to .
-
Click + Create Project.
-
Enter the required information for Project name, Organization, and Location.
-
Click Create.
Create a service account
-
Open the Navigation menu and go to .
-
From the projects list at the top of the page, select the project that you created earlier.
-
Click Create service account.
-
In the Service account details section, enter the following:
-
Service account name: Enter a name. Copy and store the name of the account. You'll need it later.
-
Service account ID: You can keep the auto-generated service account ID or change it.
-
Service account description: Enter a brief description for the account.
-
-
Click Create and continue.
-
In the Grant this service account access to project section, click Continue. Don't add any roles.
-
Optional. In the Grant users access to this service account (Optional) section, add users who own or can access this service account.
-
Click Done.
Add roles to the service account
-
Add Service Usage Viewer role:
-
Select the project that you created.
-
Open the Navigation menu, and go to .
-
Click Grant Access.
-
Under New Principals, enter the service account address that you created.
-
Under Select a role, search and choose Service Usage Viewer. If you can't find this role, ensure that the project you selected in the earlier step is the correct project.
-
Click Save.
-
-
Add Organization Role Viewer role:
-
Select your main organization.

-
Open the Navigation menu, and go to
-
Click Grant Access.
-
Under New Principals, enter the service account address that you created.
-
Under Select a role, search and choose both Organization Role Viewer and Organization Viewer. If you can't find this role, ensure that the project you selected in the earlier step is your main organization's project.
-
Click Save.
-
Create keys for the service account
- Open the Navigation menu and go to .
- For your new service account, open the menu under the Actions column.
- Select Manage keys.
- On the Keys page, click Add key.
- Select Create new key.
- Select JSON as the key type.
- Click Create. This downloads a JSON file to your computer. This JSON contains credentials that allow the service account to access Google Workspace. Keep this file for later.
- Click Close.
Enable API access
- Open the Navigation menu and go to .
- On the Enabled APIs & services page, enable Admin SDK API, Service Usage API, Cloud Identity AP, and Cloud Resource Manager API using the following steps (if they aren't enabled already):
Click Enable APIs and services.
Search for and select an API using the search bar. For the Cloud Identity API, search for Cloud Identity.
Select the tile corresponding to the API.
Select the specific API.
Click Enable.
Configure domain-wide delegation for the service account
- Sign in to your Google Workspace Admin Console and open the Navigation menu.
- Go to .
- Under the Domain wide delegation section, click MANAGE DOMAIN WIDE DELEGATION.
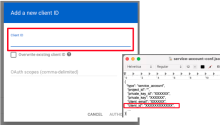
- Click Add new.
- In the Client ID field enter the client_id value. You can find this value in the credentials JSON file that you saved while creating the service account.
-
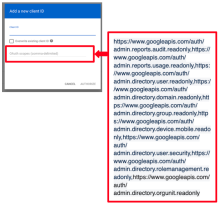
In the OAuth Scopes field, enter the following scopes as comma-separated values.
Copy\https://www.googleapis.com/auth/admin.reports.audit.readonly,https://www.googleapis.com/auth/admin.reports.usage.readonly,https://www.googleapis.com/auth/admin.directory.user.readonly,https://www.googleapis.com/auth/admin.directory.domain.readonly,https://www.googleapis.com/auth/admin.directory.group.readonly,https://www.googleapis.com/auth/admin.directory.device.mobile.readonly,https://www.googleapis.com/auth/admin.directory.user.security,https://www.googleapis.com/auth/admin.directory.rolemanagement.readonly,https://www.googleapis.com/auth/admin.directory.orgunit.readonly,https://www.googleapis.com/auth/admin.directory.customer.readonly,https://www.googleapis.com/auth/cloud-platform.read-only,https://www.googleapis.com/auth/cloud-identity.inboundsso.readonly,https://www.googleapis.com/auth/cloud-identity.policies.readonly - Click Authorize.
Add ISPM IPs to your trusted IP range
If your org has any IP restrictions for Google Workspace, you must have the ISPM IP addresses 13.52.68.184, 54.193.209.206, 13.57.96.208, and 184.72.14.192 in your trusted IP range for the integration to succeed.
Share the parameters with ISPM
-
In the Identity Security Posture Management console, go to .
- Select Google Workspace.
- Enter the following parameters:
- Source name: Enter a name for this connector.
- Super admin email address: Email address of any user who has the super admin privilege for Google Workspace in the org.
- Credentials JSON: Upload the file that you created in the Create a service account section.
- Click Submit.