Comprehensive architecture
The comprehensive architecture is a super-set architecture that represents most Access Gateway components. This architecture is designed to meet these requirements:
- Provide external access to a set of applications that are hosted inside a corporate network. They're represented in this architecture by external-use applications.
- Provide secure use to a set of applications, access from inside the network, but secured by Access Gateway. They're represented in this architecture by internal-use applications.
- Provide scalable managed access using load balancers in strategic locations throughout the architecture.
- Secure Kerberos-based applications using Access Gateway and Okta Kerberos support.
- Direct all internal network access using a proxy server.
Architecture
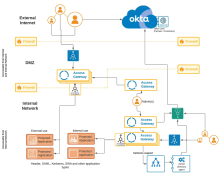
Components
|
Location |
Component | Description |
|---|---|---|
| External internet | Clients |
Traditional client browser accessing Access Gateway using known as [appN|consumer-app1].example.com URLs. |
| Okta org |
Your Okta org, providing identity services. |
|
| Okta org Universal Directory |
Okta Universal Directory, housed in an Okta org, containing users outside other LDAP or Active Directory implementations. Typically these include other customer accounts, partner accounts, and more. |
|
| DMZ | Pre-Access Gateway load balancer |
Load balancer for the DMZ-based cluster. |
| External-use Access Gateway cluster | The Access Gateway cluster provides access to applications used by external internet clients. It's housed in the DMZ. It's typically hosted in a virtual environment such as Amazon Web Services, MS Azure, Oracle OCI, or similar. See Manage Access Gateway deployment. | |
| Internal | External-use Access Gateway admin | The admin instance for the Access Gateway cluster. It's housed in the DMZ and is typically located inside the internal network. It's only accessible to administrators who are inside the internal network. |
| Post-external load balancer | The post-external load balancer manages the load between Access Gateway and the protected web resources. It's positioned between the external-use Access Gateway cluster and the back-end protected web resources. | |
| External-use application | External-use applications are protected web resources that are exposed by Access Gateway, but are physically hosted within the internal network. These applications may be Header, Kerberos, SAML, SWA, or others. | |
| Internal clients | Internal clients are users accessing applications from within the internal network. | |
| Pre-internal Access Gateway load balancer |
Load balancer for the DMZ-based cluster. |
|
| Internal-use Access Gateway cluster | This cluster is separate from the DMZ-based Access Gateway cluster and provides access to internal-use applications. | |
| Internal Access Gateway load balancer | The post-internal load balancer manages the load between Access Gateway and internal protected web resources. It's positioned between the internal-use Access Gateway cluster and the back-end protected web resources. See Load balancing. | |
| Internal-use applications | Internal-use applications are protected web resources that are exposed by Access Gateway, but are physically hosted within the internal network and are only available to internal network clients. | |
| Active Directory servers | Internal-use Active Directory servers that support Kerberos applications are required. | |
| Active Directory agents | Co-located Okta Active Directory agents, configured to communicate through a proxy, and providing user information. |
Other considerations
The following table describes where different components might be housed.
| Component | Data center |
|---|---|
| External Access Gateway cluster. Pre-external Access Gatewayload balancer | Virtual data center 1 AWS, OCI, or Microsoft Azure-based. |
| Post-external Access Gateway load balancer | Physical data center 1 Co-located with the internal-use applications. |
| Pre-internal Access Gateway load balancer | Virtual data center 2 Co-located with either internal applications or internal Access Gateway instances. |
| Internal Access Gateway cluster |
Virtual data center 2 AWS, VMWare, and others. |
| External-use applications Internal-use applications | Physical data center 1 |
|
Internal proxy server |
Virtual data center 2 Co-located with other internal servers. |
