Certificate Challenge protected application reference architecture
The Certificate challenge protected application Access Gateway architecture extends either the Firewall or Protected IP architectures and uses certificate challenge to limit access to the protected web resource. In this architecture the application is only accessible by clients validated using a very specific certificate, preloaded on all Access Gateway instances.
Certificates must be loaded and refreshed onto Access Gateway instances by Okta professional services.
This architecture meets the following requirements:
- Protects the protected web resource by hiding the internal URL from external clients.
- Firewalls protected unauthorized requests.
- Pre-configured certificate based challenge/response grants or denies access to the protected web resource
Benefits and drawbacks
| Benefits | Drawbacks |
|---|---|
|
|
Architecture
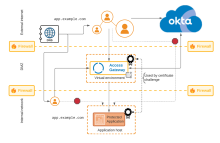
Components
| Location | Component | Description |
|---|---|---|
| External internet | External URL | External URL used by clients to access Access Gateway on behalf of the protected web resource. |
| DNS | DNS server providing DNS resolution for external URL. | |
| Between external internet and DMZ | Firewall | Firewall separating DMZ housing Access Gateway and the external internet. |
| DMZ | Access Gateway | Access Gateway cluster, located in the DMZ, uses multiple DNS servers to resolve internal and external URLs. |
| Access Gateway certificate and policy |
|
|
| Between internal internet and DMZ | Firewall | Firewall separating DMZ housing Access Gateway and the internal internet. |
| Internal network | Certificate | Custom certificate used when issuing challenges for the protected web resource. |
| Internal DNS and URL | Internal DNS server serving internal URL representing protected web resource in Access Gateway. | |
| Application | Protected web resource (application). |
