SCIM app integrations
The System for Cross-domain Identity Management (SCIM) standard allows admins to manage user and group information between external apps and Okta Universal Directory. Integrating with Okta streamlines and automates managing user accounts, credentials, and privileges between business systems. Admins can configure SCIM app integrations to use a direct cloud connection or an agent sitting on-premises.
SCIM and provisioning are frequently used as interchangeable terms, but they're slightly different. Provisioning refers to the entire process of exchanging lifecycle information, while SCIM is the standard protocol through which those exchanges are made.
Okta provisioning is a workflow best described using the CRUD operations: Create, Read, Update, and Deprovision (instead of Delete).
When events occur that impact a user's lifecycle, these provisioning functions are triggered and change the user's record in both Okta and the external app. Two examples of such events are a change in position and a software license expiring.
Admins can browse the Okta Integration Network (OIN) catalog and set the filter to search for app integrations with provisioning as a functionality. When added to an org and assigned to an end user by an admin, the SCIM-enabled app integration appears as a new icon on the End-User Dashboard.
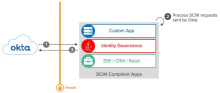
SCIM processing
- Okta sends SCIM changes to external app targets. These requests can use any of the CRUD operations to change user or group data in the app.
- SCIM compliant app integrations receive and process SCIM requests from Okta.
- The Okta User Directory reflects the updated user profile information.
To manage provisioning actions between Okta and cloud apps, admins can select SCIM-enabled app integrations in the Okta Integration Network (OIN) or configure custom app integrations. Using these app integrations, admins can connect their environments with Okta and use the provisioning features offered by SCIM:
- Sync passwords: Password synchronization helps admins ensure that a user's Active Directory password matches their Okta password. See Synchronize passwords from Okta to Active Directory.
- Map profile attributes: After provisioning is enabled, admins can set an app to be the "source" from which user profiles are imported into Okta or a "target" to which Okta sends attributes. See Attribute mappings.