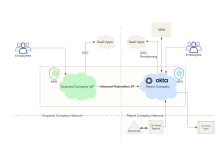
Integrate with a company that uses an external IdP
If the company you acquired uses a different identity provider (IdP) such as Azure Active Directory, configure inbound federation to sync users into your Okta org. If users from the acquired company require access to apps in the Okta org, they can authenticate using a service provider-initiated flow. Routing rules seamlessly redirect the authentication request from the Okta org app to the acquired company's IdP.
Topology
The following figure is an example of an integration between an Okta org and an acquired company's IdP. Employees of the acquired company can access shared applications in the Okta org by using their existing credentials.
Workflow
-
In your Okta org, add an identity provider. If you don't need provisioning, disable account linking.
-
Configure app sign-in policies to define access to shared resources in your Okta org.
Best practices
When you configure an IdP in your Okta org, disable account linking if possible. If you need account linking, consider Security best practices.