Integrate Okta with Windows Autopilot
This topic explains how to integrate Okta with Windows Autopilot.
Before you begin
- Set up Windows Autopilot. See Demonstrate Autopilot deployment (Microsoft docs).
- Federate your Office 365 tenant with Okta. See Typical workflow for deploying Microsoft Office 365 in Okta.
- Set up MFA in Okta. See Multifactor authentication.
- Review Office 365 sign-on rules options and Add an app sign-in policy rule.
- Ensure your end users are activated in both Okta and Azure AD and their Windows devices are registered.
Best security practices
Using Windows Autopilot with Okta may allow a device to bypass Okta Device Trust. We recommend the following best practices to minimize this possibility:
- Enable Windows Autopilot sign-on policy only for new users. You can create a separate group for new users and apply the policy to this group only.
- Once the new users have set up their device with Okta Device Trust, remove them from this group.
Start this procedure
This procedure involves the following tasks:
Add Okta MFA to Windows Autopilot
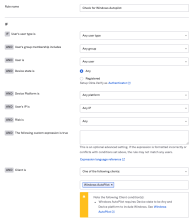
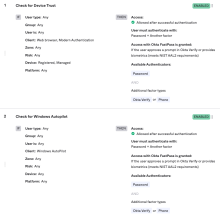
In the tab, add an Autopilot sign-on policy rule.
- Go to . The App Sign On Rule window opens.
- In the App Sign On Rule window, name the rule. For example, "Check for Windows Autopilot."
- Set the appropriate IF conditions for users and devices.
-
For the Client condition, select One of the following clients from the dropdown and then select Windows Autopilot in the field below the dropdown.
- For the Then conditions, select Access is Allowed after successful authentication.
- For user authentication requirements, select any of the 2 factor types options from the dropdown.
- Set the appropriate factor conditions and re-authentication frequency.
- Save the rule.
-
Back in the Sign-on Policy section, adjust the priority level for this Autopilot sign-on policy rule depending on when you want it to be executed.
You've now added Okta MFA to Windows Autopilot.
Optional: Set up Windows Autopilot to work along Okta Device Trust or Okta FastPass
If you are not using Okta Device Trust or Okta FastPass
You need not take any action in Okta if your org doesn't use Okta Device Trust. Windows Autopilot works out of the box with Okta as an Identity Provider. You only need to:
- Set up Windows Autopilot in your Microsoft environment, and
- Configure a sign-on rule for the Office 365 app in Okta to allow web browser clients on the Windows platform.
If you are using Okta Device Trust or Okta FastPass
If you are using Okta Device Trust or Okta FastPass, you need to create a new sign-on rule in the Office 365 app to check for Windows Autopilot with device state Any. See Task 1 of this procedure.
The Autopilot rule allows end users to securely enroll their Not Trusted devices. It checks if Windows Autopilot is available for device enrollment. If it is available, the sign-on policy uses Windows Autopilot to enroll the device and doesn't use Okta Device Trust or Okta FastPass. If Windows Autopilot is not available for the device, it applies the Okta Device Trust or Okta FastPass sign-on policy.