Create delegated flows for policy actions
For an entity risk policy rule to trigger a flow, you must first create the flow in Okta Workflows.
Before you begin
- Ensure that you have the super admin role.
- Ensure that you have access to the Workflows console.
- Identity Threat Protection with Okta AI supports only delegated flows.
Create the flow
- Open the Okta Workflows console.
- In the Flows tab, create a folder for your entity risk flows. See Folders and subfolders for more information.
- In the new folder, click New flow to add a flow.
- Click the pencil icon beside the flow name (called Unnamed by default) to edit the properties of the flow. Give your flow a unique name and an optional description. For example, Risk Policy - Low (Notify).
- Click Add event in the flow builder interface and select Delegated Flow.
- Click Add app action or Add function to add and link the cards that execute the remediation actions when the flow is triggered. See the following section for some sample remediation flows, or you can view other Workflows templates and tutorials at the Okta Content Library.
- When your flow is complete, click Save.
- Click Flow is OFF and toggle the flow to ON. You can also choose if you want to save all data that passes through the flow. This option is useful for debugging and auditing completed flows.
Repeat this procedure for each remediation action that you want for your entity risk policy rules.
Active delegated flows used in entity risk management count towards your limits for the number of flows and executions. See Workflows system limits.
Sample remediation flows
The following examples are some simple examples of flows that you can implement as part of your Continuous Access enforcement policies.
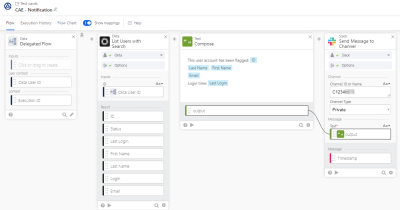
Slack notification
This delegated flow takes the user ID and pulls specific details from your Okta directory for that user. The information is combined into a message that is sent to a Slack channel to notify administrators of the incident.
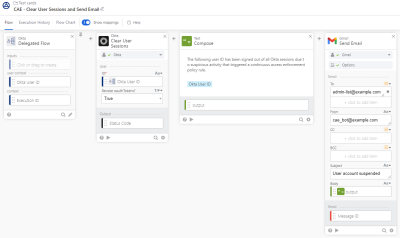
Clear user sessions and send an email notification
The goal of this sample remediation flow is to automatically remove all active IdP sessions and revoke any OIDC and OAuth tokens issued to the user. The final step includes sending an email out to a predefined list of administrators.
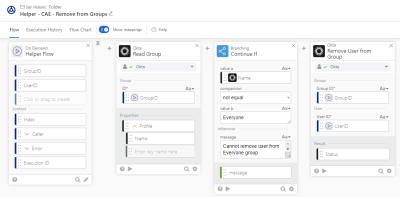
Remove the user from all memberships and deactivate their account
This is a more advanced remediation flow. It uses a helper flow to remove the user from all existing groups (the exception being the Everyone group to which all users must belong). The For Each function iterates for every group the user belongs to. The Group ID is passed to the helper flow along with the Okta User ID.
Then the flow adds the user to a group that's reserved for at-risk accounts. Finally, the user account is deactivated, preventing any sign-on activity until the risk is investigated and addressed.
The main delegated flow calls this helper flow for each group where the user is a member, to remove the user from the group. A branching Continue If function card handles the exception for the Everyone group.
These are just a few examples of Okta Workflows that can be implemented for a violation of an entity risk policy. The complexity of your delegated flow depends on your org's standards and available connector options and what you need to meet your notification, monitoring, and remediation requirements.