Kerberos overview
This overview describes the components, flow, and version requirements for integrating Kerberos-based Windows applications and Access Gateway. For more information about Windows Kerberos architectures, see Kerberos application reference architecture.
Architecture
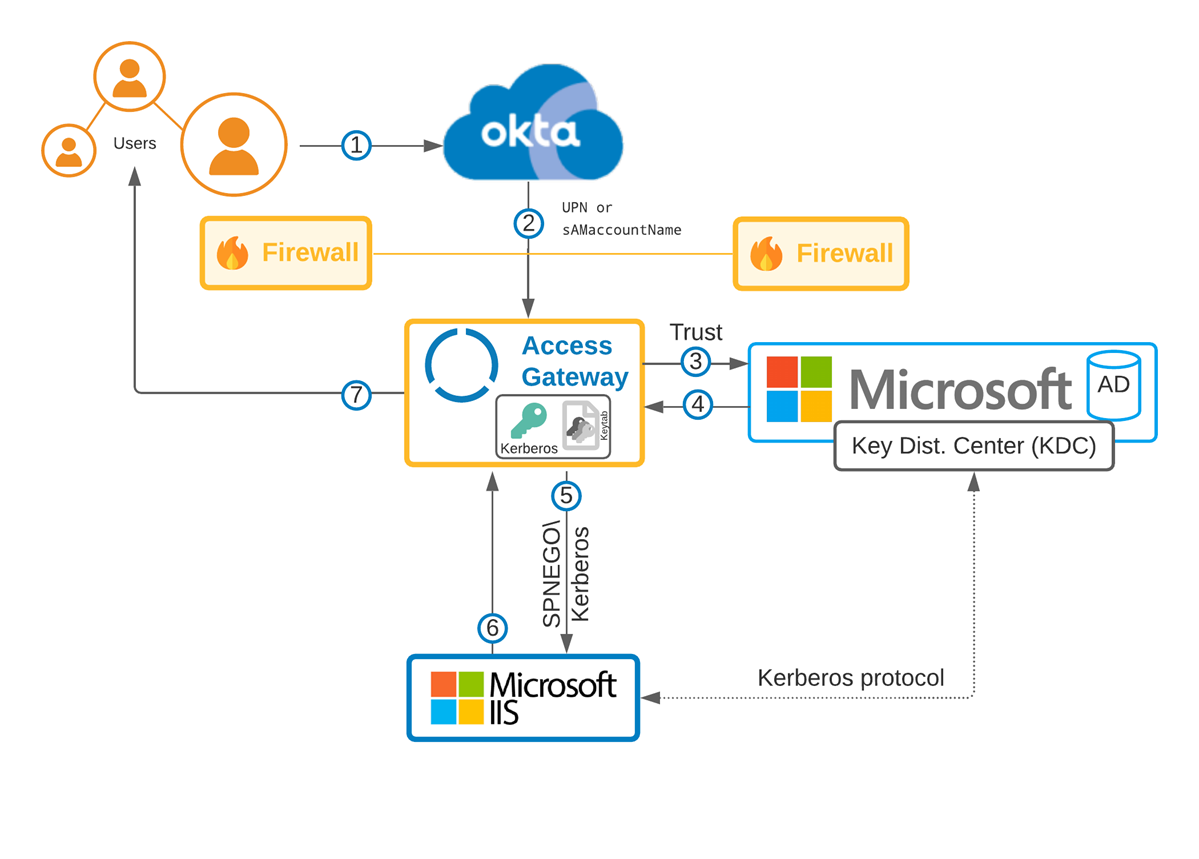
Flow
- The user signs in.
- Okta sends the user's identity to Access Gateway.
- Access Gateway accesses the predefined Key Distribution Center (KDC) with credentials.
- KDC returns a Kerberos ticket.
- Access Gateway redirects to a backing application.
- The application returns a completed request.
- Access Gateway performs rewrites and returns the request to the user.
Components and requirements
| Component | Description and requirements |
|---|---|
| Access Gateway | All versions of Access Gateway support Kerberos. |
| Microsoft IIS IWA or OWA IWA |
Supported versions:
|
|
Dynamic Name Services |
Configure Access Gateway to use Windows DNS. See Add Access Gateway to Windows DNS. |
|
Windows Access Gateway service account |
The account in the Windows domain that the Kerberos service uses. See Create a Windows Access Gateway service account. |
|
Keytab |
A keytab is used when configuring an Access Gateway Kerberos service. See Create keytab. |
| Okta Access Gateway Kerberos | Configure the Kerberos service instance. See Add Kerberos service. |
| External URL | The external URL shown in the Access Gateway Public Domain field. |
