Client certificates
A client certificate is a type of digital certificate that is issued by a certificate authority (CA). Mobile device management (MDM) software issues client certificates to devices using Okta as a CA, or the customer's own CA (referenced in Okta as "provide your own CA").
How does Okta use client certificates?
Okta uses client certificates to determine if a desktop device (macOS and Windows only) is managed or not.
When a device successfully authenticates with Okta FastPass, Okta binds a client certificate to the device (not the user) and attests certificate installation by creating a digital signature with the client certificate and validating it on the server. The Okta server uses the management attestation in the Okta FastPass protocol to satisfy the managed condition in the app sign-in policy.
How does client certificate binding work?
To verify that client certificates are securely deployed, client certificates can't be reused by a device if it was deleted from the Okta Universal Directory, or used by more than one device. To achieve this:
-
The client certificate is bound to the device after successful Okta FastPass authentication.
-
The client certificate is bound to the device, and not to the user.
-
A single client certificate can't be deployed or used from multiple devices.
How does the CA affect client certificate binding?
Client certificate binding rules are different, depending on the certificate authority (CA) that issues the client certificate:
-
Okta as a CA:
-
Okta CA manages the lifecycle of the client certificates, so Okta doesn't need to rely on the certificate revocation list (CRL) to perform certificate status validation.
-
The client certificate is revoked on the 91st day after issuance if it is not used in a successful Okta FastPass flow. 90 days provides time between the deployment of the client certificate and enabling an app sign-in policy (management attestation) with the client certificate.
-
Revoked client certificates can't be re-used.
-
-
Provide your own CA:
-
Client certificates are issued by an external CA, so Okta uses the CRL to check the certificate status before processing management attestation signals in Okta FastPass. For this to work, Okta expects the CA and client certificate to include the CRL extension.
-
During the management attestation evaluation if the client certificate is identified as not active in the CRL, Okta marks the device as not managed.
-
Similar to Okta as CA, the client certificate is bound to the device the first time the device successfully authenticates with Okta FastPass.
-
For Windows, client certificates should be in the current user certificate store and not the machine store. If using the local machine certificate store is unavoidable, ensure that no elevation is required for the user to access the private key.
For macOS, select the appropriate level to deploy the client certificate:
-
To ensure all users of the device are managed, select Computer Level.
-
If you want only MDM-managed users of the device to be identified as managed, select User Level.
Ensure the client certificate is available to all applications. See Use your own certificate authority for managed devices and SCEP MDM payload settings for Apple devices.
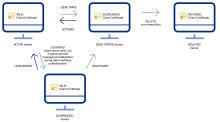
How does the lifecycle status of a device affect certificate binding?
Depending on the lifecycle status of a device, a client certificate might be valid, suspended, or revoked.
For security reasons, a client certificate is associated with the device throughout the lifecycle of the device. It can't be used for any other device.
The following table describes the state of the client certificate during each stage of the device lifecycle:
|
Device lifecycle status |
Client certificate state |
Description |
|---|---|---|
| Active | Valid | A client certificate is bound to the device after successful Okta FastPass authentication. The client certificate is valid, so the device user is treated as "managed". |
| Suspended | Valid | The client certificate is valid, but user authentication cannot provide management attestation to satisfy the app sign-in policy "managed" condition. |
| Deactivated | Suspended | The client certificate is valid, but user authentication cannot provide management attestation to satisfy the app sign-in policy "managed" condition. |
| Deleted | Revoked | When a device is deleted from the Okta Universal Directory, the client certificate that was associated with that device is revoked, so it can no longer be used to provide management attestation from any device. To use the same device in the future, delete the client certificate from the device, and then re-deploy a new client certificate to it. |
Related topics
Configure Okta as a CA with static SCEP challenge for macOS with Jamf Pro
Configure Okta as a CA with static SCEP challenge for Windows using Workspace ONE
Configure Okta as a CA with dynamic SCEP challenge for macOS with Jamf Pro
Configure Okta as a CA with delegated SCEP challenge for Windows with MEM
Configure Okta as a CA with delegated SCEP challenge for macOS with MEM