Replace Desktop Device Trust with Okta FastPass
You can't modify Device Trust after you upgrade to Identity Engine. Use Okta FastPass and Okta Verify instead.
After the upgrade, your existing Device Trust authentications (mutual Transport Layer Security authentications, or mTLS) continue to work on Identity Engine.
Any app sign-on policy Device Trust conditions are translated to Device: Registered, Managed conditions in Identity Engine. If the valid Device Trust certificate is present on the device, the device is registered and managed. If a certificate doesn't exist on the device, or if it exists but isn't valid, the device is unmanaged.
Start this procedure
Verify that Device Trust works
After the upgrade, Device Trust is enabled. Okta FastPass isn't enabled yet. The end-user experience is the same as on Classic Engine. If a user attempts to access an app that is protected by a device condition, Okta challenges the browser to present the Device Trust certificate, and then validates it. After validation, the user can access the app account.
Don't remove Device Trust yet. You can't revert this action.
- Verify that your Device Trust configuration migrated to the Identity Engine:
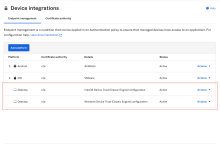
In the Admin Console, go to .
- Click the Endpoint Management tab.
- Verify that the listed platforms match the device types you identified in the pre-upgrade procedure. See Turn off Device Trust on mobile devices.
For example, if Windows and macOS Device Trust were enabled in your Classic Engine, these platforms are listed on the Endpoint management page.
- Verify that your app sign-in policy includes a rule for registered and managed device conditions:
In the Admin Console, go to .
- Click App sign-in.
- Select the policy that you want to verify.
- One of the rules in the policy should specify Device: Registered, Managed.
- View the following System Log events, to verify that Device Trust is still working:
- Authentication
- DisplayMessage: Authentication of device through a certificate
- EventType: user.authentication.authenticate
- Enrollment
- DisplayMessage: Device Trust certificate enrollment
- EventType: user.credential.enroll
- Issuance
- DisplayMessage: Device Trust certificate issuance
- EventType: pki.cert.issue
- Revocation
- DisplayMessage: Device Trust certificate revocation
- EventType: pki.cert.revoke
- Renewal
- DisplayMessage: Device Trust certificate renewal
- EventType: pki.cert.renew
- Authentication
- Verify the following items on multiple operating systems:
- All existing use cases work. For example, users with Device-Trust-enabled desktop devices are able to authenticate.
- All app sign-on policies migrated successfully. For apps that are protected by Device Trust, a rule must include a condition for Managed and Registered.
- Use existing mTLS certification.
- Certificate renewals work (if applicable).
- New enrollments work (if applicable).
Enable Okta FastPass for some users
Consider the following scenarios and read about Device registration.
| Okta Verify isn't installed. | When the user tries to access a Device Trust-protected app, the org sign-in page appears. Okta probes the user's device for Okta Verify. After the user enters their username, Okta completes an mTLS challenge and the management attestation is gathered from the Device Trust certificate on the device. |
| Okta Verify is installed on the device, but the user only has an Okta Classic Engine account. | When the user tries to access a Device Trust-protected app, the org sign-in page appears. After the user enters their username, Okta completes an mTLS challenge and the management attestation is gathered from the certificate on the device. |
| Okta Verify is installed on the device, but the user doesn't have any account. | When a user tries to access a Device Trust-protected app, they're prompted to add an Okta Verify account. The authentication flow completes without mTLS authentication because the Device Trust status was provided by Okta Verify. |
- If you disabled mobile Device Trust, complete this procedure: Configure management attestation for mobile devices. Then, go to the next step.
- Prepare enterprise devices for Okta FastPass. Push the latest version of Okta Verify app to all desktop devices. Using your MDM, turn on inline enrollment for some users. See Device registration and Managed devices. See Okta Verify configurations for macOS devices, and Okta Verify configurations for Windows devices for information about the EnrollmentOptions flag.
- Make sure a certificate authority (CA) is configured and management certificates are deployed to all desktop devices. You can use Okta as a CA, or provide your own CA. See Configure a Certificate Authority.
If you provide your own CA, follow these steps:
In the Admin Console, go to .
- Click the Certificate Authority tab.
- Deploy management certificates to the devices.
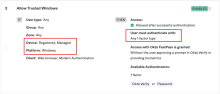
- Update your app app sign-in policy. Verify that you have a managed rule for each applicable platform. Change the User must authenticate with value to Any 1 factor type:
- Allow Trusted macOS:
- Platform: macOS
- Device: Registered, Managed
- User must authenticate with: Any 1 factor type
- Allow Trusted Windows:
For details about setting up your app sign-in policy, see Configure an app sign-in policy for passwordless authentication with Okta FastPass.
After you complete this step, users are automatically prompted to enroll in Okta Verify the next time they access Okta. If a user installed Okta Verify and added an account (enrolled), they now use Okta FastPass to sign in. Therefore, the device is trusted. If the user doesn't have an Okta Verify account, they use the Classic Engine Device Trust certificates to sign in.
- Allow Trusted macOS:
- Enable Okta FastPass. This is a global setting, but only the following categories of users have access to Okta FastPass:
- Users with inline enrollment (set up in step 2)
- Users who registered in Okta Verify and have a management certificate (set up in step 3).
When you enable Okta FastPass, make sure you select the Okta FastPass (all platforms) checkbox before you deactivate Okta Device Trust.
- Verify these scenarios when Okta FastPass is enabled:
- Users who aren't enrolled in Okta Verify but are enrolled with Device Trust should be able to successfully access apps that are managed.
- Users who aren't enrolled in Okta Verify should be able to enroll in Okta Verify.
- Users who enrolled in Okta Verify from a managed device should be able to successfully access apps that are managed.
- Users who enrolled in Okta Verify from an unmanaged device should be able to access apps the same way they could before the migration.
Enable Okta FastPass for all users
Encourage users to enroll in Okta Verify and have management certificates on their devices. Ideally, all users have an Okta Verify account with Okta FastPass enabled so that you no longer need Device Trust.
- Request all users to enroll in Okta Verify or deploy it on all user devices.
Share this information with your end users:
- Verify the following items:
- Okta Verify is deployed to all users using your MDM.
- All users have a management certificate, using your MDM (see Task 2, step 2).
- All user access apps from devices with Okta Verify, and not Device Trust) (see Task 1, step 3).
Remove Device Trust and decommission your IWA servers
When all of your users are using Okta FastPass, you can remove Device Trust.
- View the System Log events to ensure that Device Trust signals no longer exist. (See Task 2, step 3). If Device Trust signals exist, migrate these users to Okta Verify. Any users who don't use Okta Verify will be impacted.
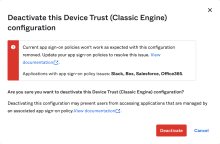
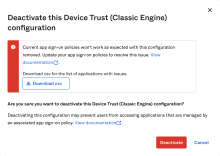
- Deactivate Device Trust:
In the Admin Console, go to .
- Click Endpoint Management.
- For the required Platform, click .
If you receive an error when you try to delete the platform, see Device Trust deactivation error .
- Click Deactivate.
- Delete Device Trust:
- For the Inactive Platform, click .
- Click Delete.
- Decommission the IWA servers from your infrastructure, and then remove the Device Registration task from your devices using your preferred tool.
Related topics
Turn off Device Trust on mobile devices